We have made it! After several months of posts, we have come to the series summary on CCTV Acquisition. Thank you for joining us on this journey.
It’s now time to look back and remind ourselves of some of the key points, and understand how incorrect acquisition may affect the future tasks required.
Digital Multimedia Evidence
During the series, we have concentrated on public or privately owned CCTV. However, many of the challenges, solutions, and workflows are also valid for CCTV and video surveillance systems owned by your agency or company. You may work within Law Enforcement and have CCTV in various venues. As such, the management of that digital data is easier to control effectively. With organizational responsibility, any requirement for its use can be made much simpler, with all issues regarding integrity and authenticity documented within a Standard Operating Procedure (SOP). The same can also be said of Body Worn Video (BWV).
Although these devices are often within a controlled environment, the management of the video data through any viewing, assessment, processing, redaction, and demonstrative creation must be managed the same way. And yes, it’s the same for covert surveillance video, drone footage, and video from the Helicopter.
It is all just Digital Multimedia Evidence (DME) after all. The key to getting it right, and ensuring the questions regarding integrity and authenticity can be answered, is considering the importance of the words.
Deal with video as Evidence. Preserve it as volatile Digital data. Acknowledge that Multimedia must be decoded accurately for it to be interpreted correctly.
CCTV – The Beginners Guide
In CCTV – The Beginners Guide, we broke down the various components of a common CCTV system and learned that the data is not often managed in a standard way. Due to the damage caused by an uncontrolled surveillance industry, the starting point of many video investigations is often proprietary data. Luckily, with the forensic video decoding provided by Amped Engine, and built into our other applications such as Amped Replay and Amped FIVE, there are solutions to many of these proprietary formats.
The first stage, though, is finding where the data is.
CCTV – Search and Trawl
In Search and Trawl, we looked at how to identify the presence of CCTV. Camera locations can change all the time, so although a local database is often a good starting point, it may mean a manual search.
The importance of footage triage and immediate viewing was discussed. If the footage is not quickly identified as being relevant, other footage yet to be acquired could be overwritten. After locating the CCTV, the first method of acquisition is simply collecting the footage from the owner.
CCTV Recovery
In CCTV Recovery, the system user is given the responsibility of evidence acquisition. Therefore, there are many important considerations that they may not be aware of.
The most important is that they preserve and export the native digital data as required by the priorities and parameters of the investigation. To aid in this, we looked at the difference between CCTV-time and real-time and how any offset can be calculated with the Time Calculator in Amped FIVE.
We also considered that to ensure the right evidence, the person given the responsibility of evidence acquisition must have competency. Simply selecting the wrong format can change the data to such an extent that critical evidence can be lost.
Public Submissions of CCTV and Video Evidence
In recent years, many organizations have begun requesting that data be shared via the Internet to avoid any requirement to attend. In Public Submissions of CCTV and Video Evidence, we detailed some of the challenges that this now brings.
The public may not realize that changing the format is altering the evidence, so detailed guidance should be given to ensure the data can be used effectively.
Law Enforcement submission systems must not restrict the data types as CCTV does not conform to standard formats.
We also looked at how the storage of any submitted data must be controlled and follow the guidance on digital evidence. Data must be individualized immediately to ensure integrity of the data, and no changes to the structure or filenames must occur.
Navigating a CCTV Device and Reviewing Video
In Navigating a CCTV Device and Reviewing Video we moved up a gear and actually started to take control of a Video Surveillance System (VSS).
We looked at the importance of identifying the system and taking detailed notes. Systems can be expensive, and many have been untouched for some time. The risks involved were explained.
Whilst navigating a device interface, we examined the presented data before playing back the footage required for review.
Closed-Box CCTV Acquisition Using Storage Media
After a review comes the Closed-Box CCTV Acquisition Using Storage Media. Why is it called closed-box? Because we don’t need to open up the system.
Competency must increase, along with having some equipment to hand. We need a digital storage device to export the data onto. The increase in competency comes from a requirement to ensure that the data is recovered correctly. You are responsible. If you get it wrong, it can be a much bigger problem.
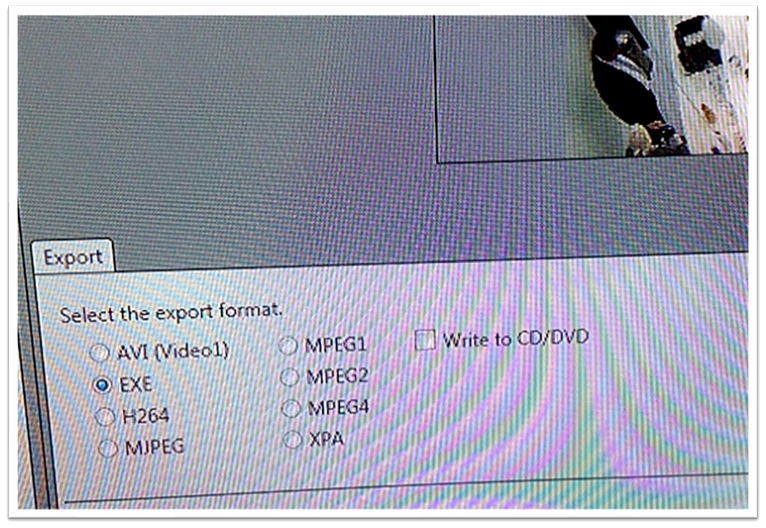
We used the CCTV device interface to identify what was being recorded. We looked at the video stream type and the compression being used. After reviewing the data, we identified two different backup options, time-based backup, and file-based backup. We also discovered two different formats, AVI and H264.
Selecting them all allows us to analyze the data acquired to identify the most reliable method for further acquisitions.
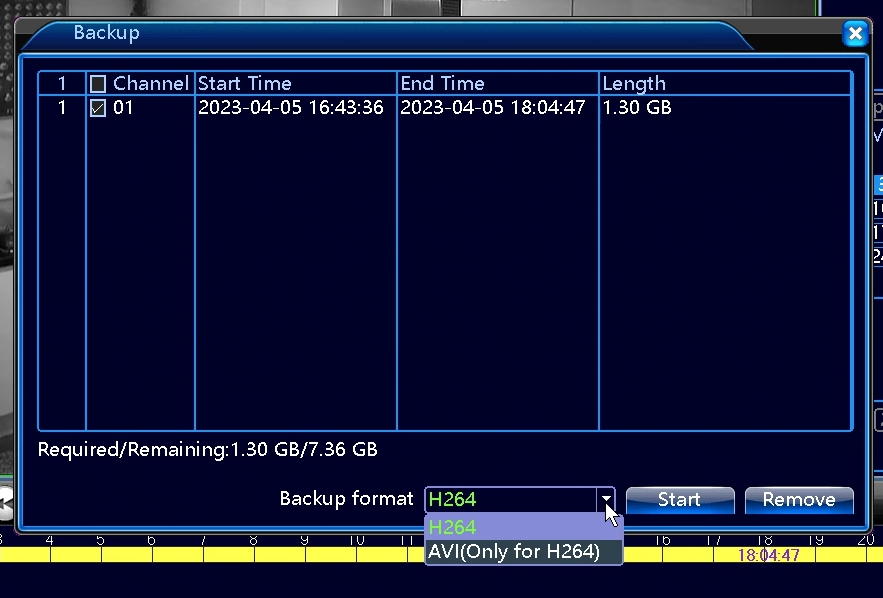
After completion, we identified that the AVI option had errors on playback, and using the time-based mode, there were frames missing.
Using the file-based mode with H264 allowed for the files to be accurately decoded and the data timestamps extracted with forensic software such as Amped Replay or Amped FIVE.
Closed-Box CCTV Acquisition Using Network Access
In the next post, we conducted a Closed-Box CCTV Acquisition Using Network Access. Here we detailed basic networking guidance and highlighted some tips and tricks to assist in making that connection between your computer and the CCTV system. Networking is often tricky, especially when requiring unrestricted data access to a surveillance device.
After accessing a device we investigated the various methods of data acquisition before downloading the files required.
After analysis and comparison of the files recovered previously, we identified some differences. Understanding these differences and identifying the visual artifacts was important, and Amped Software Support was used to ensure that this variant of the h264 format was added to the Amped Engine.
CCTV Device Removal and Replacement
It is often not possible to conduct an acquisition on the scene, so a device must be correctly removed. We looked at this in CCTV Device Removal and Replacement.
When powering down a system, the first consideration must be a backup. We looked at various data backup methods as a “just in case”, option if the internal Hard Disk Drive never boots up again! Various system shutdown options were detailed, explaining the pros and cons of each one.
Removing someone’s VSS is not something to be considered lightly. If it is necessary, there is often a requirement to replace it temporarily. Guidance was then given on some considerations for this.
Open-Box Acquisition Using the Internal Hard Disk Drive
Up until now, we have not opened the CCTV device, but in Open-Box Acquisition Using the Internal Hard Disk Drive, it was time to get the screwdriver out.
Access to the inner workings of the device was covered before detailing Hard Drive cloning and forensic disk image creation.
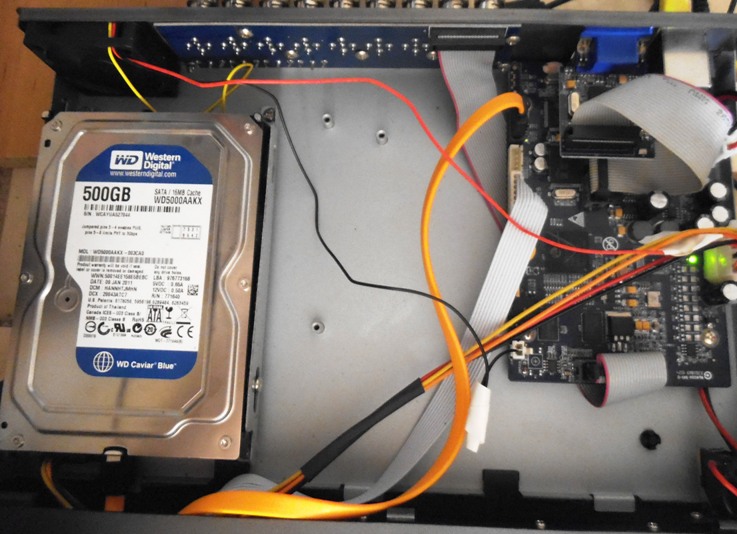
The workflow of identifying steps was covered, as making the wrong decision may increase the work required. If the files are visible on the drive, then using Copy & Verify in Amped FIVE could save you a lot of time.
HDD recovery software was used on a HDD where the files were not visible to standard operating systems. We identified that this software was unable to extract raw streams and only allowed the streams to be placed into the old AVI container format.
File carving and raw data analysis were also considered, along with some guidance on creating known test data in order to assist in data interpretation.
There are always times when something is better than nothing, and we looked at this also. Using chunks of the raw data and simply extracting the I-Frames is sometimes just enough to make an investigative decision.
Remote Acquisition Using a Mobile Device
A recent challenge has become the Remote Acquisition using a Mobile Device. Although not necessarily a recommended method, it is something that is being completed regularly by CCTV owners due to the simplicity of “App” access and then sharing.
It is not recommended for evidential use due to the many variables involved and the often reduced quality of the recorded sub-stream.
Many of these issues were looked at, including a new one of files being downloaded but not being placed correctly into a media container. Consequently, we had to rebuild the data to make them playable.
Acquisition from a Cloud-based Service Provider
Another more modern challenge is the Acquisition from a Cloud-based Service Provider. Cloud-based systems are becoming popular with small premises and homeowners, but they do bring complications when the data is required to be used as evidence.
In this post, we looked at various systems and conducted an acquisition using the Nest type. After conducting several acquisitions, we evaluated and compared the data to establish accuracy. As Nest is part of the Google family, we also utilized the Google Takeout service to acquire all video data.
With several different methods of data acquisition available, the importance of analysis and validation were therefore discussed. Also, with many of these systems coming from a group of large companies, controlled Standard Operating Procedures (SOPs) for dealing with such devices were recommended.
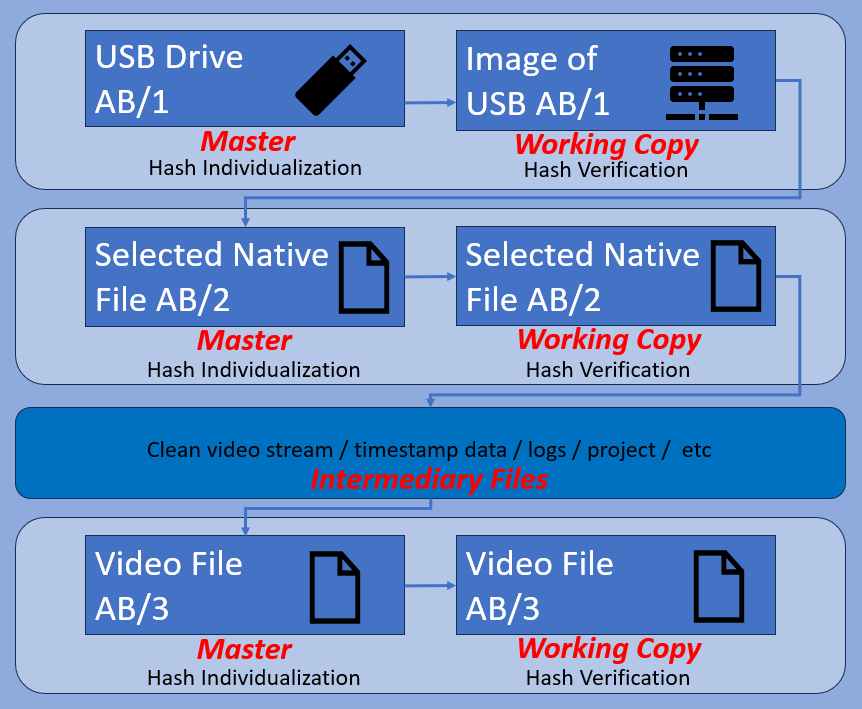
The Creation of Master and Working Copies after CCTV Acquisition
An important and often misunderstood stage is The Creation of Master and working Copies after CCTV Acquisition. Understanding where an item originates from, how it was created, and what has been used to create it is the key to ensuring that what is presented as evidence has integrity.
The first stage is the individualization of any data. This ensures that a simple comparison can be made to prove that item A is the same as item B.
An item can only be a master, the first created object, or a working copy of it. If a master is used to create another form of media, if the data changes, then it is a new master.
There is no such thing as “court playable”, or “press release version”. If it changes it’s a new exhibit, and the creation of that exhibit must have integrity.
Viewing CCTV after Acquisition
With the working copies created, in the last post, we looked at Viewing CCTV after Acquisition. The 4 stages of viewing were broken down and detailed. After looking at the initial assessment of the data we moved to the visual evaluation of the evidence. The next stage is the processing required to complete the tasks followed finally with the review prior to release or court use.
Each stage is there for a purpose and ensures that issues can be addressed early, and perhaps further data acquired before it’s overwritten.
The Importance of Correct Acquisition
Many may wonder why we started this series. It comes from several years of witnessing the increase in poor CCTV evidence. The support team at Amped Software receives hundreds of files monthly, and there are common threads in many of the conclusions.
- An object or area in a video is unable to be restored effectively because the data being used has been incorrectly acquired.
- The structure of the video, and in particular the timing, cannot be fully relied upon because it has been incorrectly acquired.
- A task or question relating to the video cannot be completed fully because the initial starting point is a transcoded version of the original video.
- The video is unable to be decoded correctly or presents damage, missing frames, etc, because no assessment of the data was completed after the acquisition, and this is where the corruption likely would have occurred.
It is simply not possible to start a forensic process correctly when the starting data is already compromised.
We also find that many areas have split the role of acquisition and analysis. What appears to happen then is that the acquisition teams attempt to save time by just removing the device or internal HDD. This saves them a few hours, but to the expense of the next department. Saving 5 hours for one team costs another 15 hours! Through every stage, the next stage must be considered.
Forensic Video Processing
We hope that some of the hints, tips, tricks, and guidance will go some way to ensuring that you start with the right data, ensuring your evidence has integrity, and that further processing can easily be completed. This brings us nicely to that processing stage, and we briefly looked at this in the Master and Working Copies post.
Processing is when anything is done to a master video exhibit. What you can do, and how, will be controlled by your organizational procedures, but you are limited by the starting data.
Forensic video processing is documented in many different ways, but if the basics are maintained, it’s actually very difficult to get wrong.
- Science
- Math
- Research
- Objective decision making
- Repeatable
- Reproducible
- Explainable
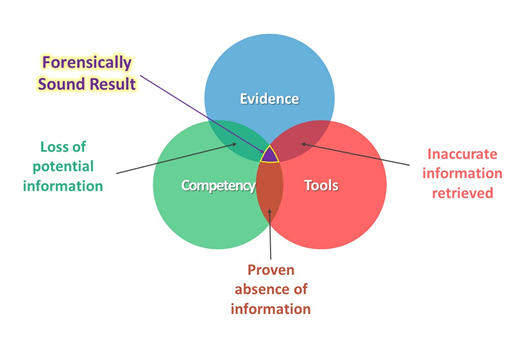
Many of these are detailed in the Video Evidence Principles, written by our CEO, Martino Jerian. The second section of the principles, written specifically for first responders, technicians, and analysts, drills down into many of the core components required when conducting any forensic video process.
Perhaps, in the future, we will post something on the tasks or questions often asked of video and show how, with Competency, the right forensic Tool, and the correctly acquired Evidence, it is possible to obtain the best result.
Until then, it is time to say goodbye with a list of equipment that may be useful when conducting acquisitions. We have broken it down into 3 levels.
- Level 1: Basic recovery and acquisition using external media.
- Level 2: Network access, with the ability to assess data on-site.
- Level 3: Internal HDD acquisition and device removal and replacement.
Equipment Suggestions
Note: This is not a definitive list, it is a starter for you, that can be adjusted and added to where necessary.
Level 1: Basic recovery and acquisition using external media
- USB mouse, with PS/2 adaptor for legacy systems.
- Selection of optical disks: CD-R, DVD-R, you may also find some other disk types will come in handy, such as DVD+R.
- Selection of USB flash drives: varying sizes, manufacturers, and speeds. Older systems may not support large-capacity drives. Consideration must be given to how the drives are formatted. Many systems will not recognize NTFS.
- USB Hard Drives: 1Tb and 2Tb may be sufficient, with consideration again to how drives are formatted. Drives with data protection may not be supported.
- Smartphone: ability to conduct time checks and calculate time difference offset at the scene. Also suitable for the capture of photographs of the system, camera views, user interface etc.
- Optional: flash media cards, SD, MicroSD, CF etc.
Level 2: Network access, with the ability to assess data on-site
All from Level 1, plus:
- Laptop and software/hardware.
- Modern Windows, but consider either a dual boot with 2 versions, or virtual machines.
- Amped Replay or Amped FIVE
- Partitioning and formatting software
- Drive imaging software
- ISO reading software
- Network analysis software
- Proprietary software specific for CCTV
- External optical drive (if not built-in)
- USB write blocker
- Video capture hardware
- Network cables, patch and crossover
- USB extension cable
- USB A-A cable
- HDD caddy key
- Compressed air can
- Torch
Level 3: Internal HDD acquisition and device removal and replacement
All from Levels 1 and 2, plus:
- Toolkit
- IDE / SATA write blocker
- Selection of Internal SATA HDDs, a smaller selection of older IDE drives is also beneficial
- Forensic HDD Cloner
- Forensic DVR Acquisition Software
- Replacement DVR/NVRs
…and if anyone tries to tell you that CCTV acquisition is easy, just send them this series!