The CCTV Acquisition blog series continues here with the creation of master and working copies after CCTV acquisition. Incorrect handling and exhibit referencing can cause huge delays to the Criminal Justice System. These errors may even lead to miscarriages of justice, so it is vital that all acquisition, movement, processing and changes are correctly documented and verified.
This is something that has to be taken seriously, with internal policy and guidance documents written to ensure evidence integrity, rather than following any outdated or incorrect procedure.
In the series so far we have acquired original, native evidence. It has either been recovered from, and produced by the video owner, or we have acquired it ourselves using any of the methods covered in previous posts:
- CCTV Recovery
- Acquisition using Storage Media
- Acquisition using Network Access
- Device Removal and Replacement
- Using Internal Disk Drive
- Acquisition using a Mobile Device
- Acquisition from a Cloud-based Service Provider
We may also have the video on a police system after it was submitted by a member of the public or recovered and uploaded by a first responder. We have also looked at this in a dedicated post.
Manual handling, processing and tracking of digital data is quite easy to control. When using an automated service, however, such as a Digital Evidence Management System (DEMS), it must be configured to follow the same, very basic principles of digital evidence, rather than just a way to store documents.
Digital Evidence Principles
- Principle 1: No action should change the original digital data.
- Principle 2: Access to original digital data should only be done by those competent to do so.
- Principle 3: All actions should be repeatable, reproducible and explainable.
- Principle 4: The officer in charge of the investigation must ensure compliance with these principles.
Various versions of these principles exist, with the above taken from the original UK ACPO Guidance for Digital Evidence. Although written several years ago, the principles are still valid today as they simply transfer the basic rules of evidence into the digital domain. It should go without saying that probably, the most important principle is that no changes must happen to the original. This includes filename changes or restructuring of the data components. We have looked at filenames, and the importance of these in the past. Especially when they relate to dates and times.
Export structures are also very important. Any changes to a structure can make data unreadable.
Automated systems must also ensure that the chain of custody starts as soon as possible, ensuring that integrity can be maintained throughout the items life cycle.
Digital Evidence
We start, perhaps, with one of the following forms of evidence:
- Digital Device (DVR/NVR)
- Internal HDD
- External HDD
- Flash Media Card
- USB Flash Drive
- Compressed Folder (ZIP)
- Folder of files
- A single File
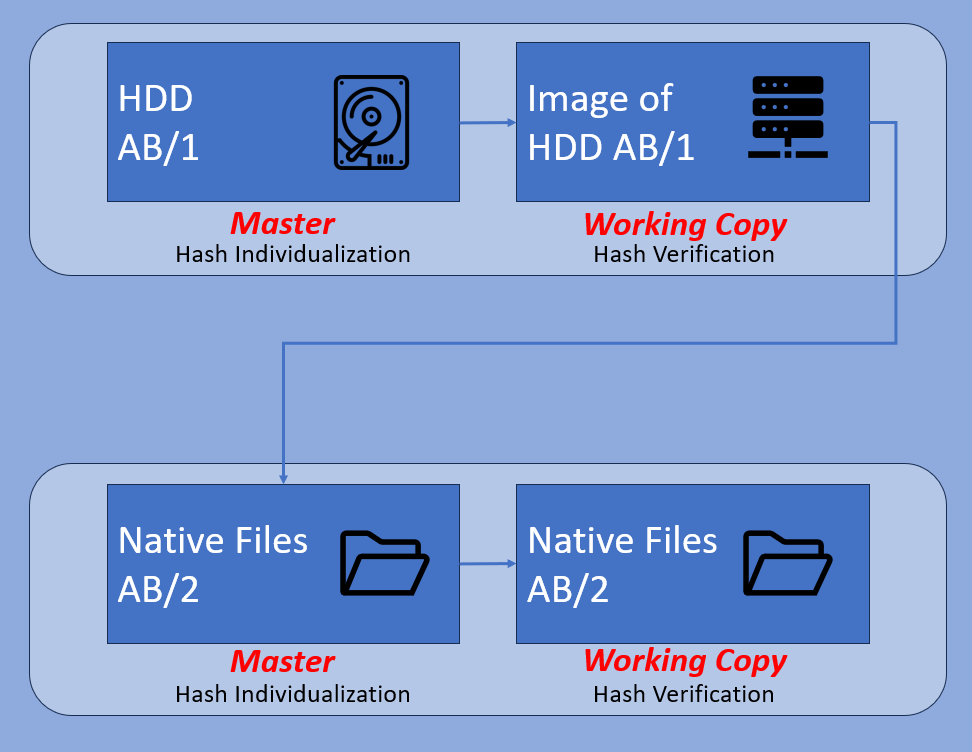
Whatever you start with is the master. There can only ever be one master but, there can be several working copies of it. This is where the process of individualization comes in.
Due to the ease of digital changes, either through evidential processing, accidentally, or even maliciously, this individualization stage ensures that any other person can verify that what is being examined is a true working copy of the original master.
An original master is not limited to an initial acquisition. If three 10-minute video files are joined together, to form a single 30-minute file, has the data changed from the source files?
Yes. The pixels may be the same, the total frame count may be accurate, the timing may have been retained. But, the file has changed. Therefore, this new file, must be referenced differently.
It is not a working copy of the three previous files, it is a new master. Where this master is stored will depend on an organization’s infrastructure and capability. It’s not possible to cover all worldwide situations for the preservation of the master. So, for this post, let us use a locally managed storage server.
Digital Device (DVR/NVR)
The first piece of evidence we will consider is a physical video surveillance device such as a DVR or NVR. It is common for such devices to be temporarily retained to facilitate video acquisition within a controlled environment.
There can only ever be a single master in this case. Even if the internal Hard Disk Drives (HDDs) are forensically imaged, as we looked at in this post, the Hard Drive data may not store recording settings. The data concerning logs and user actions may also be completely unreadable out of the device.
If the device, and internal settings, form part of the investigation, then considerable care must be taken with the master. Consideration should be given to using a clone HDD within the device and recording all interactions as we looked at here.
If only the video data is required, and the device is to be returned to an owner, then very thorough reporting and documentation must be completed. The video data acquired must be native, and supporting evidence should be retained. It is also best practice to consider the acquisition of other files if the parameters and priorities are limited in scope.
An example of this is where only a single camera view is evidentially required. It may be beneficial to acquire 10 minutes from all other views to answer any questions further during the investigation. This is also helpful when the footage concerns an incident where timing is relevant. Obtaining the other camera views for the same time as the incident may answer questions regarding timing structure that would be unable to be identified if only the incident was retained.
Native Acquisition
When the acquisition has been completed, the files, documentation, notes and recordings should ensure that another analyst does not doubt that the video data is the same as was on the device. In contrast, it would be incorrect to seize a device, capture the video signal being output from the HDMI, and then return the device. This may have been easier and quicker, but the video data being output is NOT the native evidence. The data has completely changed since it was on the device. As a backup, or as a last resort, this method may preserve a version of the event, but it is not the original.
In all the workflows, to make things easy to understand, let us use the reference AB/number to indicate a unique exhibit. If the reference changes, it’s a new exhibit.
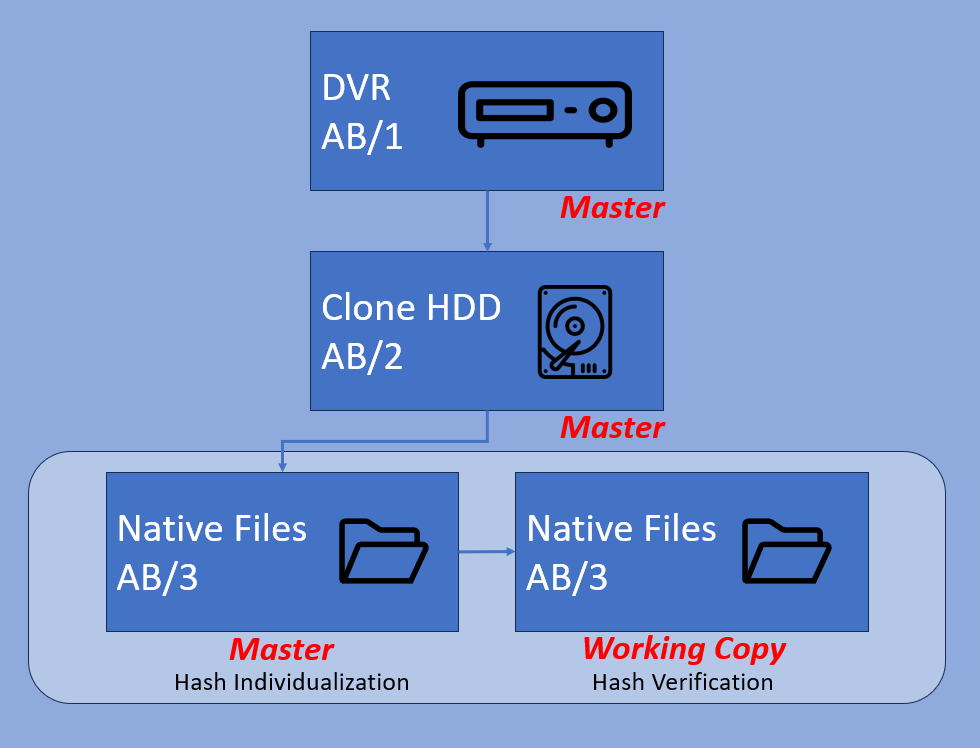
Here, the DVR was temporarily retained and produced as exhibit reference AB/1. The internal HDD was cloned to preserve the video data. This is a new exhibit as it differs from the DVR. The video data may be the same, but it does not contain the operating system of the DVR. This HDD clone is produced as exhibit reference AB/2.
The DVR is used to facilitate the acquisition of native files from AB/2. These files are a small part of the data that forms AB/2. As a result, they must have a new reference – AB/3. Now comes one of the most important stages in digital evidence management.
Individualization and Verification
We have talked a lot about this stage over recent posts but let us look further into it now before we examine other forms of evidence.
Hash individualization is the process of calculating a small and unique alphanumeric value based upon all the input data, through the use of a cryptographic algorithm.
Hash verification is the process of calculating another value using the same algorithm and comparing it against a previous calculation to verify the integrity of the data.
It is beyond the scope of this article to dive deep into hash algorithms but, for individualization and verification, even those algorithms that are susceptible to engineered collisions are generally considered to be safe to use for this purpose.
A good reference document is the SWGDE Position Paper on the use of MD5 and SHA1 Algorithms.
We must now individualize the files that form AB/3. The easiest tool, that incorporates all the various hash functions, including copying and report creation, is the Copy and Verify tool in Amped FIVE.
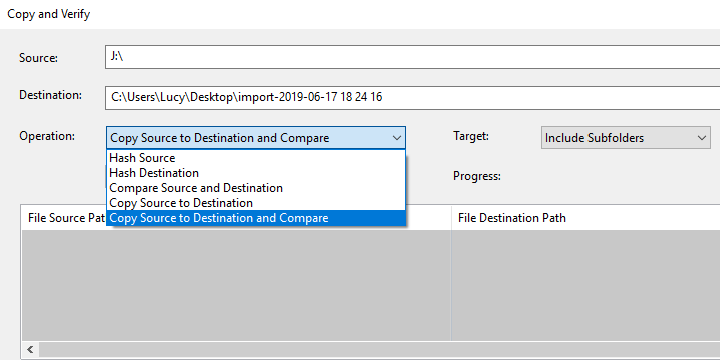
You can read all about that tool here in the release post.
The final hashing stage is the storage of the values. This is again vital, as any other analyst must be able to use those values to verify that the files being examined are the same as what was originally acquired or created. Let us now move on to the next example covering master and working copies.
Internal HDD
A Hard Disk Drive removed from a device is the master exhibit. Remember though that the physical device is merely the storage system for the evidential data. This data can be preserved, moved, and duplicated. It’s still the same exhibit, as nothing has changed. Again, suppose the physical disk forms part of the investigation, perhaps due to writing on the disk or other marks/damage. In that case, the container must be referenced separately from the data held within.
We looked at Internal HDDs in this post and explained that many devices from CCTV systems do not have standard partitioning. Therefore, the data is often not readable as individual files. In this case, data carving, or the use of dedicated DVR HDD software is required to extract the native files and again this was covered in the dedicated post.
In this example, the native files have been acquired directly from the HDD Image. It is important to remember that if a software application is used to facilitate this process, the files must be native recordings. If the software has transcoded the video, or standardized the video in any way, perhaps by removing the internal data timestamps, then the original HDD Image must be retained.
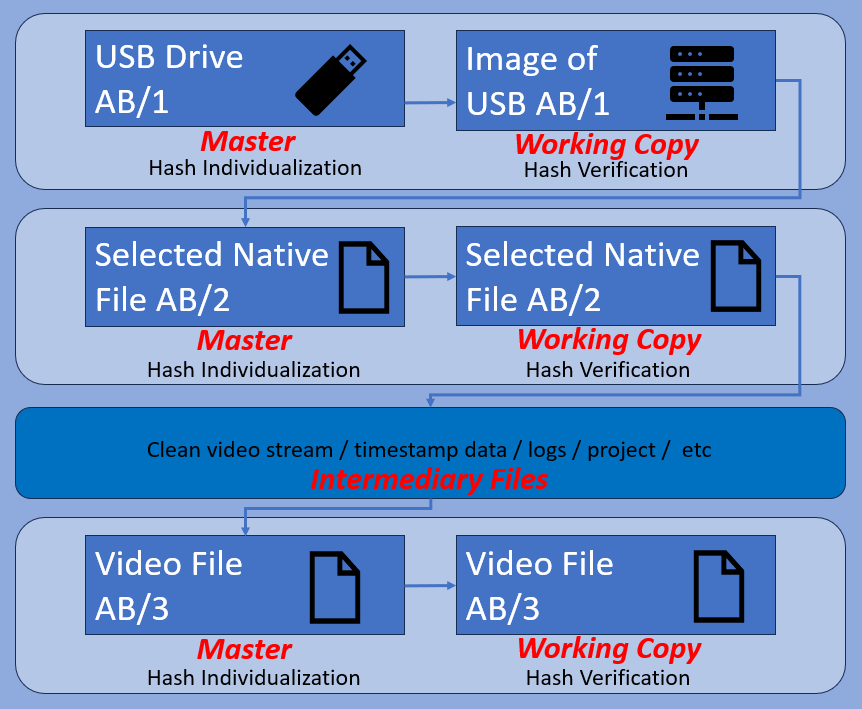
External HDD
An external HDD will usually be attached to a computer via a data transmission method such as USB. The difference from an internal HDD is that these almost always have a Windows or Mac-compatible partition system and, the data within it will be file-based. Because of this ease of communication, a write-blocker must be utilized before connection.
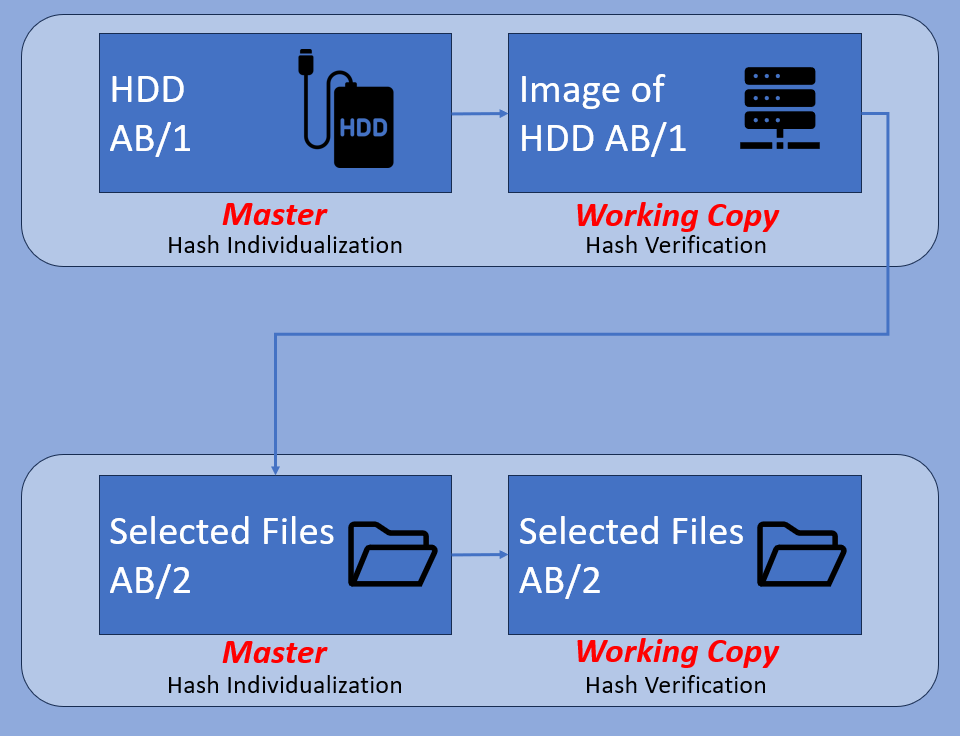
It would be completely acceptable to work from a mounted image in this case. In the diagram above, this would be the working copy of AB/1. Several investigators could be viewing the footage from this device. When an incident or event is identified, those files will be separated. There could be several different events separated. These selected files must be newly produced, and their originating source (AB/1) documented.
Flash Media Card
Solid-state media cards are commonly used in phones, dashcams, sports cameras and also CCTV cameras. We looked at them in a previous post.
The same important rule applies here regarding the protection of the original data. To connect the device to the PC via a write blocker.
Media cards can store data in several different ways. Therefore, it is important to recognize the difference between a device being used for temporary storage to aid in the transfer of data, and one that is being used for initial storage.
For example, a dashcam may utilize a MicroSD card to store the initial recordings. As the device requires a specific structure, it may format the card to support this. The result is that some of the recorded data may not be visible to standard operating systems, in a similar way to many CCTV devices. Because of this, it is important to acquire a forensic image of the card to ensure that no data is missed in any non-forensic copy-and-paste procedure.
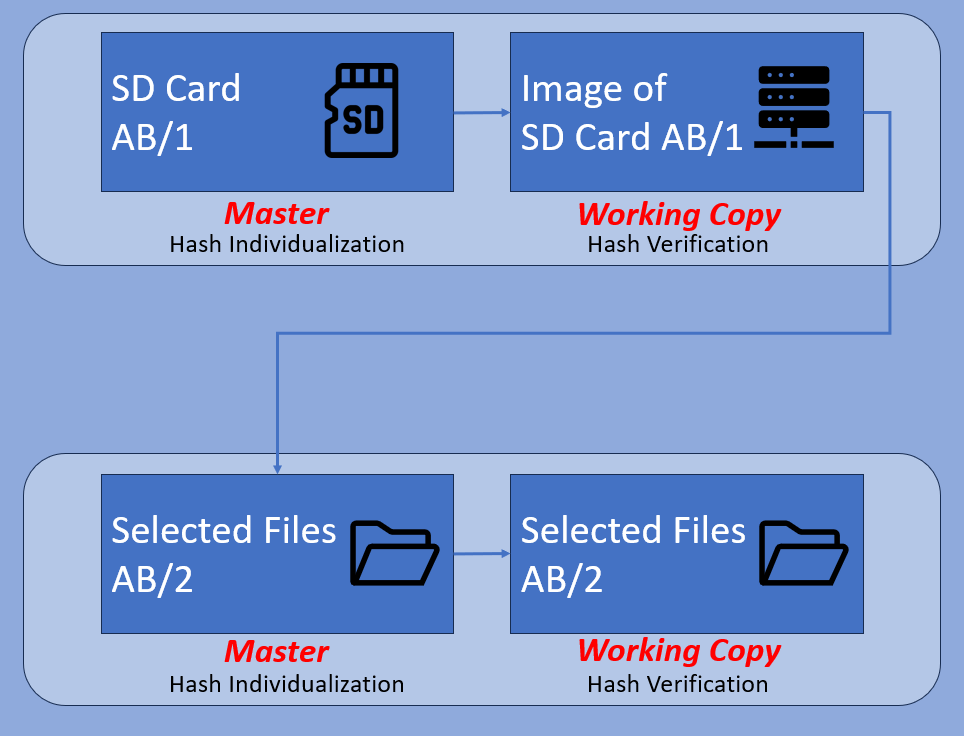
If the full image was never taken, then any hidden partitions would never be discovered. Perhaps containing index or GPS data. If the full image was never taken, and only selected files removed, then comparison with other files could not occur.
USB Flash Drive
These are very similar to External HDDs but their commonality and ease of use bring about further challenges.
The first is the presence of malicious code and viruses. We looked at using a USB device for the acquisition of CCTV data in this post and stated the importance of fully cleaning the device before use. This is simple when the acquisition is controlled and completed by a competent person.
However, in many instances, it is the CCTV owner or a first responder with little training that provides the device to be used for temporary storage. What is hiding on the device? Where has it been used? Could it contain something that may harm your computer?
The second, as always, is to consider taking a full image of the device rather than simply copying and pasting selected files. This is digital data, and you can never go back and check data that you did not retain.
Having a full forensic image of the device ensures that all data is retained, it can be compared, and any corrupted or deleted files can be viewed and possibly recovered.
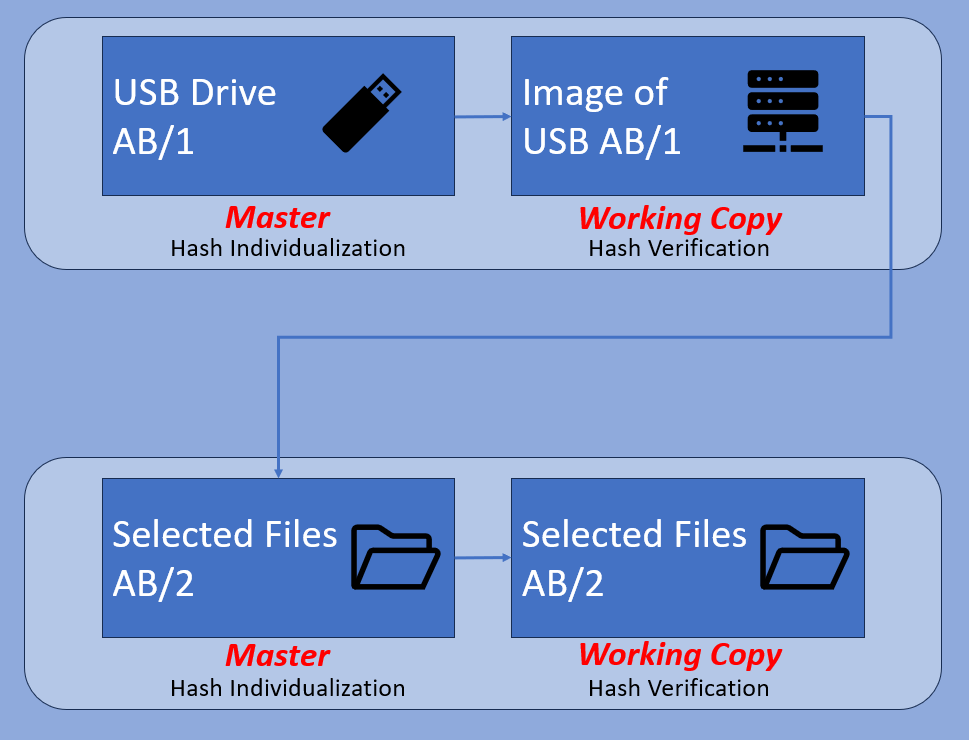
Before we move on to files and folders, let us briefly look at a forensic image of a USB drive used for the temporary storage and movement of CCTV files. We looked at Forensic Imaging software in this post.
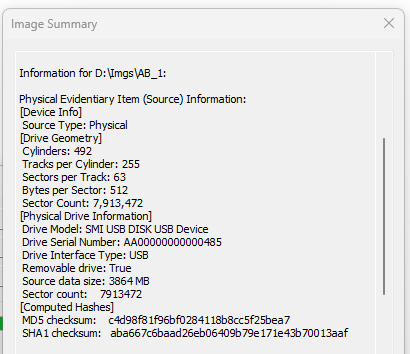
Forensic Image
After an image is created of AB/1, a full summary is saved including the image hash for verification.
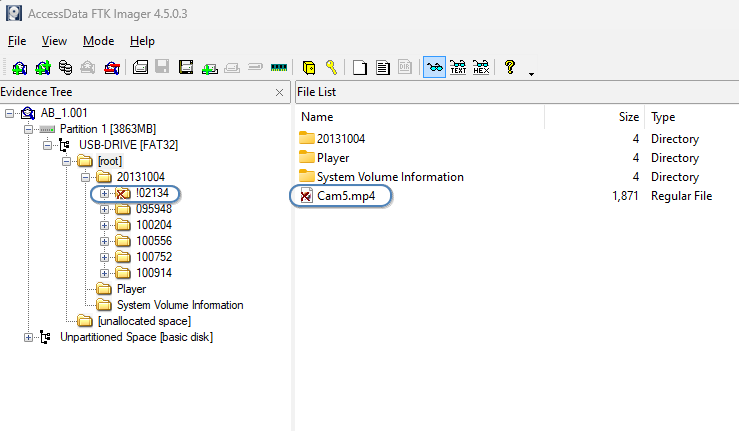
When the image is loaded into the software, all the data is visible, including any files that perhaps did not copy to the drive correctly or that were marked for deletion.
We can see in the image above that a full export folder is marked with an X, and a separate video file is also marked. These are not visible in Windows but could they be important? Images can be mounted, so that Windows see it as a drive, and also files and a hash list of files created.
Compressed Folder (ZIP)
We are now moving on to files and folders. Let us look at master and working copies of a compressed folder first. There are many different compressed formats, Zip, Rar, 7z etc. They all wrap up a collection of files and folders into a single file.
This single file can be thought of as a storage box, just like a drive. Therefore it’s easy to hash this independently before the files are uncompressed. Any movement of this zip file can then be verified through a single hash comparison.
Many DEMS are now creating compressed files and there is an increase in public submissions of zipped/compressed files.
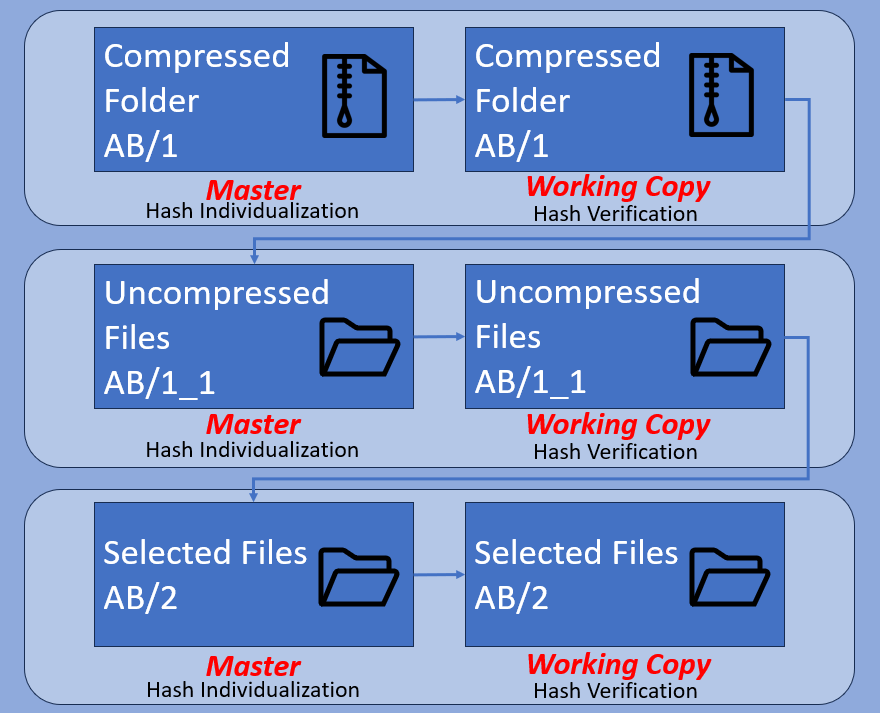
It is worth remembering that whenever there is a change to the data, the calculated hash value will change. If the change is expected, then the files exhibit reference must also change.
The importance of the middle step, the individualization of the uncompressed files cannot be overstated. If these are not listed and individualized, there would be no record of any other files’ existence as the compressed folder will only have a single hash value. The included files must be individualized as soon as possible.
Folder of Files
In many of the previous examples, we have ended with a folder of files. Consequently, we now need to use these files.
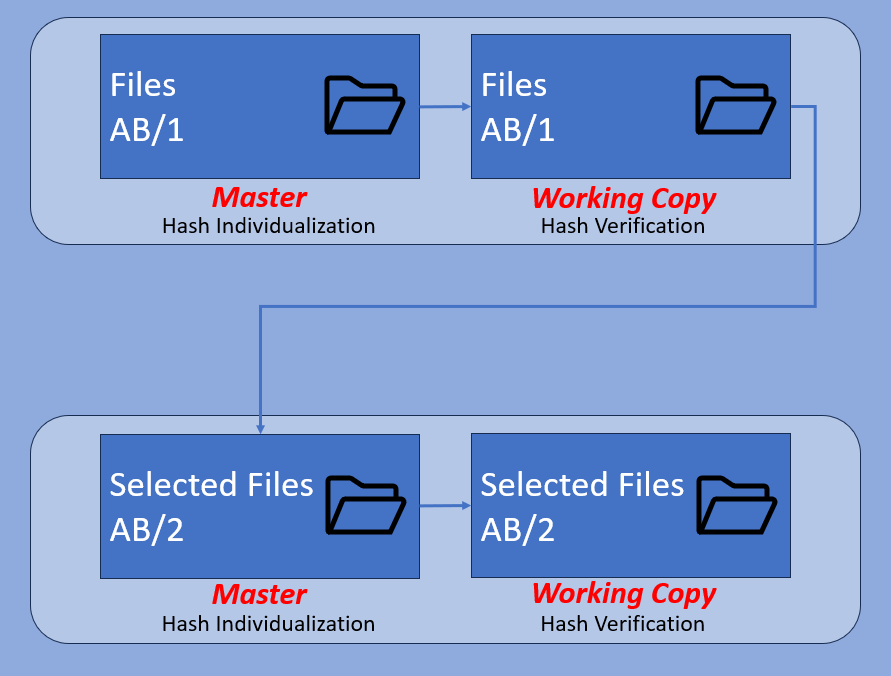
We often start with a large folder full of video files, index files, and perhaps a proprietary player with all its various components. It’s common to only need a small number of these files after they have been reviewed. We may also not need the proprietary player. If a selection is then copied into a separate folder for evidential use, then this must be referenced as a new exhibit.
Single File
It is the same for a single file.
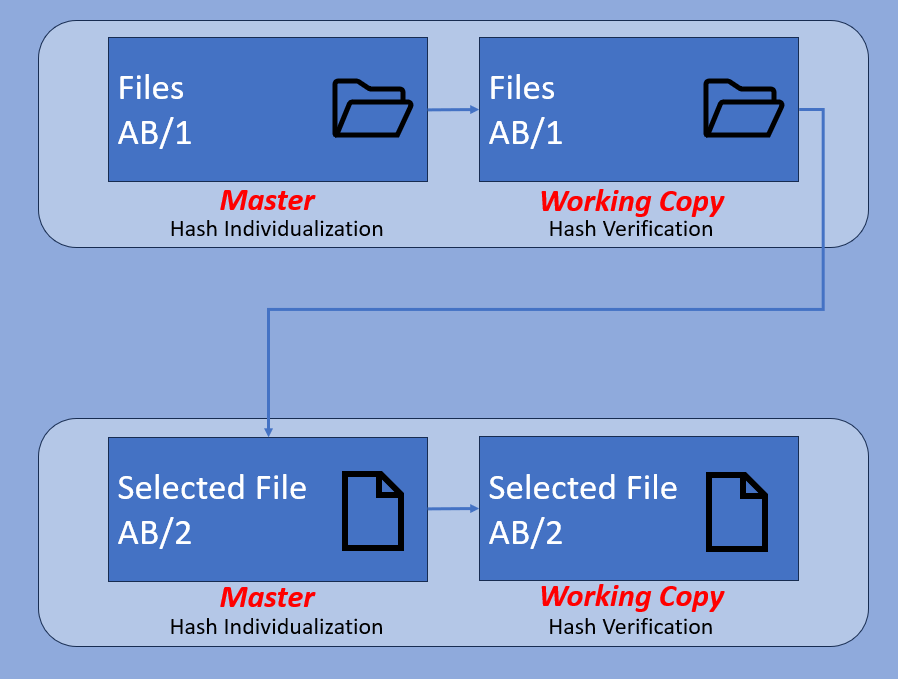
The single, selected file is not a working copy of the files originally produced. There were other files in that exhibit, and they are linked together. There could be other cameras, deemed as not relevant. Also, there could be a player that was not used. There could be index files that were not decodable by the investigator.
Multiple Exhibits
Now that each original exhibit has been looked at, what about the exhibits that are produced? Again, it is very simple. If the hash changes, then it needs a new reference as it’s a different file. This is the crux of the problem with multiple different versions of files.
We regularly see files referenced AB/1-Court Copy or AB/1-Defence Copy. Neither are AB/1 as they are different. They have been transcoded or redacted. They have been produced from AB/1, but where is that?
Let’s look at a simple, single-file first.
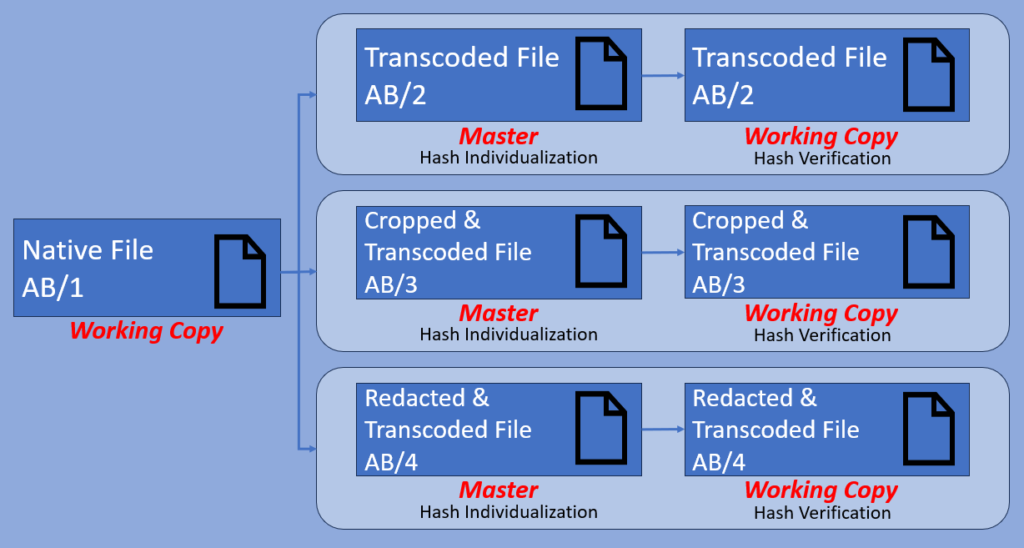
We have started with a single, working copy, native video file. From this file, we have produced three other exhibits.
- A transcoded file
- A version that has been cropped, and then transcoded
- A version that has been redacted, and then transcoded
These are the files produced as demonstratives, and each one is different.
What about 2 full folders of files?
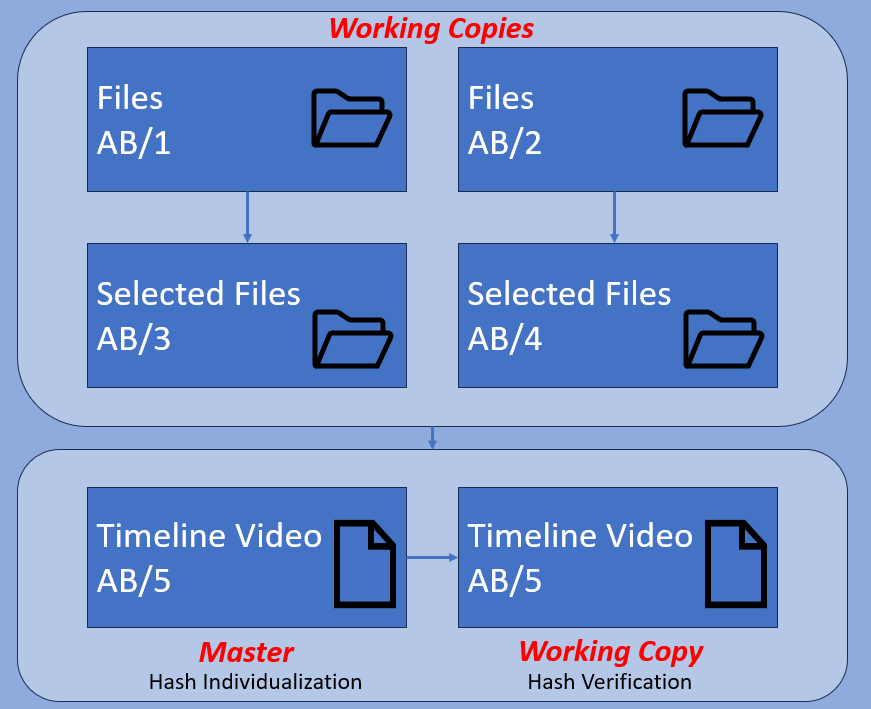
In this example, we have selected the relevant files from 2 working folders. Using those files we have created a timeline video for court use. Read more about the timeline filter here in the release post. This timeline video is a new master exhibit and must be referenced as such.
Any analyst tasked by the court to evaluate, answer questions or present digital multimedia evidence should be able to produce documentation that charts the acquisition, what is being used, unused and importantly, what has been created from the data acquired. Consequently, any other analyst should be able to identify what is an original exhibit, and what has been created from it.
Master and Working Copy
You may have noticed that throughout the various examples, there are two versions of media exhibits. The master, and then a working copy. There are no other versions and no “playable version”. Also, there is no “redacted version” and no “suitable for press version”.
It is this that causes so many problems. If it’s new, if the hash is different, then it has a new reference. If it’s the same, it has the same reference. It is just a working copy.
Is it good practice to label working copies? Of course – as long as the documentation, and importantly the hash validation, can prove that it is a correct working copy. In forensic software such as Amped FIVE, there are safeguards in place to avoid overwriting or changing a file if the master is accidentally used. It is though best practice to always use a working copy to cover you against data loss or corruption.
Summary
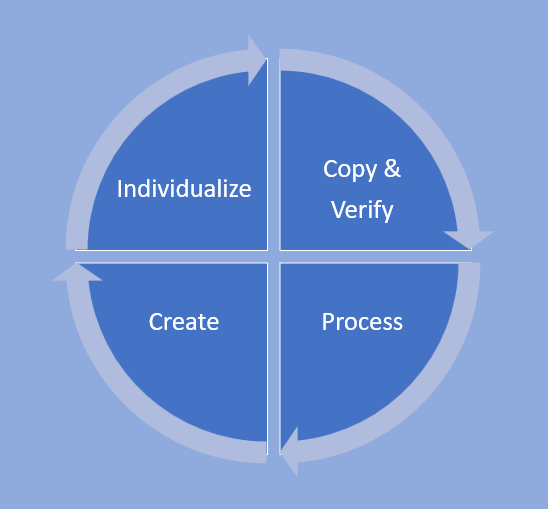
You must also remember that it is often a cycle.
You may need to create files that go on to create other files, such as the timeline video we looked at earlier. This is especially important with proprietary CCTV where data processing can cause many questions surrounding image integrity.
This guidance does not relate to intermediary files. These are only the building blocks of new multimedia. These files form part of your processing workflow.
The retention of these files are important though to prove the integrity of the exhibits produced.
In all the examples shown here, we have only started with a maximum of 2 master exhibits. With visual evidence, especially that obtained from CCTV, being so common, you will often start with many more. You may then create several video and image exhibits from them.
By compiling a digital multimedia evidence tree early on, and documenting what files have been created from what, many problems will be overcome at a later time when it comes to identifying the integrity of the various video and image exhibits.
This has been an important post in the series. We can do everything correctly, but if devices, folders and files are not correctly managed, then mistakes can be made. By understanding the importance of exhibit tracking, and correctly documenting the flow of multimedia throughout an investigation, these mistakes can be minimized.
Next time in the CCTV Acquisition series we will be looking at the controlled viewing of CCTV after an incident.