Welcome back to our blog series on CCTV Acquisition. In this latest article, we shall be looking at the public submissions of CCTV and video evidence. CCTV and video are now covered under the umbrella of digital data. In the series so far, we have learned about some of the many challenges investigators face when acquiring that data in an evidential manner. It is a long way from simply removing the VHS tape from the machine. Read on to find out more!
The importance of the acquisition stage cannot be overstated. With the data being overwritten or unprotected, you will often only have a very small window of opportunity to preserve it. However, the CCTV acquisition must also be completed in a manner that will not affect the integrity or authenticity of the evidence. Any errors in this stage will affect the reliability of the exhibit within the investigation.
We learned, in the last post, about the importance of ensuring that any CCTV owner being requested to acquire footage is aware of what is required and have competency in completing the export. They are, after all, conducting an evidential process on the investigations behalf.
Technology has assisted the export process over recent years. Thus, the movement of data is completed quicker and the storage media is larger. But, with the advances in technology, further challenges are encountered.
Public Submissions
It is now much easier for video evidence to be recaptured, changed, and then shared. As such, many investigative organizations are accepting the public submission of CCTV, dashcam, and video evidence. This has been designed to expedite the recovery of the footage, negating the requirement of officer or technical staff attendance. In this post, we will look at some of the issues that this now causes. Also, we will offer some guidance to ensure that the integrity and authenticity of the submitted footage is preserved. Any doubt cast upon the item can have a large detrimental affect on its reliability.
The first step is to avoid many of the problems to start with. Simple online guidance, whether displayed on a web page, or as a message on any uploading online portal, can go a long way in avoiding difficulties in the future.
The person submitting must supply their details. They must be aware that they may be required to give evidence as a witness, even if they are only supplying the footage and did not actually witness the captured event themselves. If submitting several files, the source of each file should be given, such as identifying concurrent recordings, different cameras from the same system, or from different systems. Most importantly, they must state if the footage is original, or if it has been changed in any way. This includes the renaming of files and transcoding, which is the change from one digital format into another.
If an uploading facility is supplied to the public, rather than email, then the automated individualization of the received files is paramount.
What Does this Mean for Public Submissions?
Remember that all files must have integrity, in that it can be proven that the file has not changed. When a digital file is received within an organization, it is a relatively simple process to automate the calculation of a unique alphanumeric value using an algorithm.
We will learn more about this process later in this blog series. However, the resulting value can then be associated with the file. It ensures that at any time after the public submission, any person, anywhere can run the same algorithm. A matching value will verify that the file is the same as was submitted. If this process is not automated, a manual creation must be completed before any movement of the file, viewing, or processing. Remember, this is digital evidence and must be handled and treated as such.
Many data management systems were designed for digital documents. So many aspects of handling Digital Multimedia Evidence (DME), may have been overlooked.
Footage Evaluation during Public Submissions of CCTV
It is then vital that any footage submitted is evaluated as soon as possible along with any associated information received. The reviewer must have the competency to identify some of the easy-to-recognize signs of originality.
The first is the naming style. Dashcams, cellphones, and, of course, CCTV usually have a naming convention. Something like this (without the file extension):
“12112022_193406-194510.”
To see something like what follows, however, may suggest it has been edited or it has had some form of human interaction:
“Man Commits Robbery.”
The user may not realize that simply changing the filename can cause issues if that data was the only record of the date and time information. That date and time information may be of vital importance in cases where it places a certain person in a location at a specific time.
Next comes the file extension. This is the part after the name and usually depicts the format of the file.
00123.AVE
This extension would suggest, to a person with competency in multimedia evidence, that this is a file originating from a specific type of CCTV. However, if this person received 00123.WMV, this may suggest that it is not an original CCTV export. It is rare for CCTV to use the WMV format. A closer look may be necessary.
Along with the competency of the reviewer, this person may benefit from having access to software able to assist in the initial viewing and analysis of submitted multimedia.
Footage Evaluation with Amped Software
Software such as Amped Replay was designed specifically to play the original proprietary and standard video. It performs a quick analysis and creates forensic derivative evidence for crime reports or media releases.
One of the many functions of Amped Authenticate is the ability to quickly analyze images for traces of manipulation. With image editing now so easy, when someone submits an image to law enforcement, the reviewer needs an application to check its authenticity.
First Viewing
When evaluating a video, it must be a digital copy of the video submitted. Later in the series, we will discuss storage, master copies, working copies, the continuity between those, and the creation of any derivative evidence.
This initial viewing is vital. It can affect the decisions of any investigation. Importantly, it can identify any need to urgently visit the location and to conduct a legitimate CCTV acquisition when mistakes have been made by the person submitting.
We must, at this point, reiterate the importance in the original native recordings. We mentioned earlier about the renaming of a file to “Man Commits Robbery”. The footage received may show the scene and the events. However, due to how it has been sent, it may not be suitable for further use, such as a clothing comparison.
Screen Snapped Re-recordings
During several recent forensic video events, analysts from around the world identified that one of the biggest challenges being faced in legal proceedings today is the public submission of screen-snapped re-recordings.

The recording of a CCTV screen or computer monitor with a cell phone is often required in the immediate hours after a serious incident when the requirement to trace or identify a person or vehicle may protect life or property. It is only a backup though, as the visual data has very limited integrity or authenticity.
The early identification of a re-recording ensures that a request for the original footage can be made or trained personnel dispatched to acquire it.
A visual review may also identify signs of editing and transcoding. Members of the public may believe that they are helping law enforcement by conducting some edits or changing it to a standard video format. However, only those with acquired necessary competency must complete this, and all within a controlled forensic environment.
Cellphone Apps
Another challenge faced by public submissions is the increase in cellphone app access to CCTV. Many Video Surveillance Systems (VSS) now have the ability to link with an app. What is viewed, and then saved on a cellphone or tablet, is often of a much lower quality than what was actually recorded by the system. It is these, poor-quality streams, that are then sent to the police, rather than the high-quality original footage.
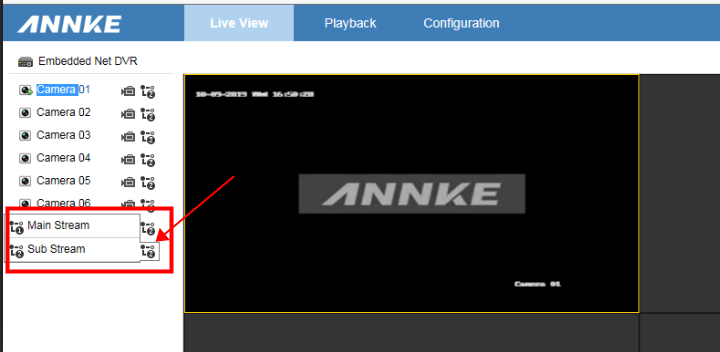
These sub-streams may also have different recording frame rates. These may affect timing, motion and speed analysis within Forensic Collision Investigations.
Without internal processes being put in place to avoid these many challenges, investigative decisions may be made on footage of poor quality and with little evidential worth when considering their originality or accuracy to the events.
When a poor-quality video is evaluated for the recovery of a license plate, for example, you can only make the correct decision when you have the original footage, and when the decision maker has the right knowledge and tools.
Conclusion
The public submission of CCTV and video can save time. It can provide law enforcement with early intelligence to further an investigation. However, the public must be given the guidance to submit the correct material. Law enforcement must put the right procedures in place. They must ensure that any files submitted can be used to their full advantage.
Without identifying the errors early, any lack of integrity or authenticity may not be discovered until it’s too late.
Next time we will move on with, “Navigating a CCTV Device and Reviewing Video“. It’s time to start looking at the recording device before we attempt a CCTV acquisition ourselves. Until then, stay safe.