This is the first in a series of posts on use cases for our products done by Jim Hoerricks. In this post, we’ll see the issues on authenticating images from social media.

As a general rule, there are three basic ways of authenticating an image prior to trial. The first way involves the photographer attesting to the image’s authenticity. The second way requires someone depicted in the image to say that, “yes, that’s me and that’s the scene as I remember it.” The third way gets a bit more complicated. The third way brings in a third-party to authenticate the image. It is hoped that this third-party authenticator’s findings are grounded in science and solid methods. Sadly, this is not often the case.
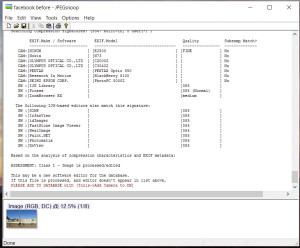
The scientific authentication of images that are taken directly from a camera are complex enough. But when the image is uploaded to social media, the images are changed. This change shows up in many freeware programs – like the one depicted to the right – as a warning that the image is processed or edited. Many unskilled technicians use a report like this as a basis to declare an image not authentic. This can cause problems in court.
Take this scenario for example:
- Take a picture using your own camera.
- Upload that picture to your social media account.
- Download that picture from your social media account to your computer.
- Run it through a program like the one shown above.
The program will conclude that the image has been processed / edited. It’s right. It has. So what?
But what hasn’t changed in this example is the context / content of the photo. You haven’t “Photoshopped” the image. You just uploaded it to your social media account. Clearly, another solution is needed that can check a wide range of potential forgery scenarios. That solution is Amped Authenticate (Axon Detect in the USA).
Authenticate is a photo analysis program for tamper detection. It goes beyond image-matching to offer you a robust suite of authentication tools to certify evidence in-house. This reduces the need for external consultants, shortens turnaround time, and lets you use evidence captured by the public that is posted to social media accounts.
The need for a reliable authentication tool is quite serious. Valid results depend on solid science, not guesswork and the improper application of tools from other disciplines.
In 2010, a California prosecutor argued that a defendant deserved a 5 year sentence enhancement due to his gang affiliations. During the appeal of this decision, the defendant alleged that the arresting agency “Photoshopped” his likeness into the image that was taken from a social media account. People v Beckley, et all (B212529 – Ca. 2nd Appellate District), a rare published appellate ruling affirmed California evidence code that, “A photograph is a “writing” and “[a]uthentication of a writing is required before it may be received in evidence.” (Evid. Code, §§ 250, 1401, subd. (a).)” The defendant prevailed and the sentence enhancement was reversed.
The basic objection made by the defendants in the case was that they were added to the image. This is a very specific allegation of forgery. Unlike a blind authentication, “tell me if this image has been altered,” cut/paste/delete forgeries can be tested … even if they’ve been reprocessed by social media pages. This is known as contextual authentication. This is the power of Authenticate.
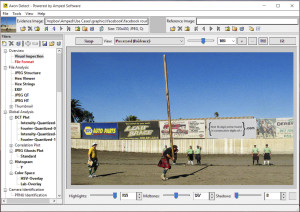
In our example, we have an image from Facebook. There’s a lot going on in the image, some of which looks quite unbelievable. But is it authentic? If not, what’s wrong? Something has been changed. But what?
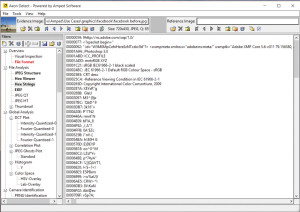
An examination of the Hex Strings filter shows the plain English word “Photoshop.” Unfortunately, this is not proof of “Photoshopping.” Taken as a whole, this bit of Hex shows the fingerprint of the Facebook upload script.
The EXIF filter view shows the Facebook profile entry. Again, it’s not proof of forgery, just that it’s been through Facebook. It’s certainly not a camera original, but we’ve yet to see evidence of tampering.
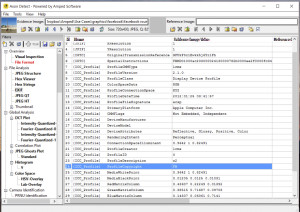
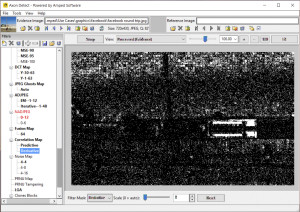
One way to find evidence of cut/paste/delete forgeries is to examine the relationships of the pixels to their neighbors. The Correlation Map filter in Authenticate displays the estimated probability map (p-map) that embodies the spatial correlations within the image. In this case, the mismatched area is displayed in white.
In a matter of a few minutes, Authenticate found the problem with the image. An area of the image had been replaced, changing the context of the image. If you are going to trial with images from social media sources, wouldn’t you want to know ahead of time if the images are authentic? In states like California, it’s not just a nice suggestion, it’s a requirement that images be authenticated prior to their introduction.
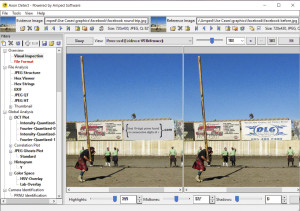
The visual comparison of the original (right), and the altered image (left) shows the changed billboard.
With over 20 different filters, Authenticate users can test a wide variety of forgery allegations on common image formats.
Wouldn’t you like to know:
- If something has been changed in the image?
- If something has been deleted in the image?
- If the image comes from a particular device?
- If the image can be found elsewhere on the Internet?
- Where the image was taken?
Wouldn’t you like a fast and reliable answer to these questions? With Authenticate, you can.
But, don’t take our word for it. We’re happy to share a fully-functional trial version with you. See for yourself how fast it is. Test it against images in your system. Create your own forgeries and see if Authenticate can spot them. Contact your Amped / Axon salesperson today, or visit our web site.