This week is Amped Authenticate‘s turn, and we are going to look at our images from a different perspective than usual, that is… their bytestream! We’ll see how Amped Authenticate’s Hex Viewer and Hex Strings filters can help you spot hidden information in your evidence images.
As most Amped users surely know, digital images contain much more than a “sequence of pixel values”. For example, we have information related to the file format, needed to properly decode and show the pixels, and we may also have a variable quantity of metadata. All this information is commonly structured according to some standard, and Amped Authenticate helps you unpack and read most of such structured information through filters like Exif, JPEG QT, JPEG HT. But what if someone added additional information without following any standard? In that case, no “interpretation” of the information can be made. Still, Authenticate provides a couple of ways for you to take a look at what’s inside the image!
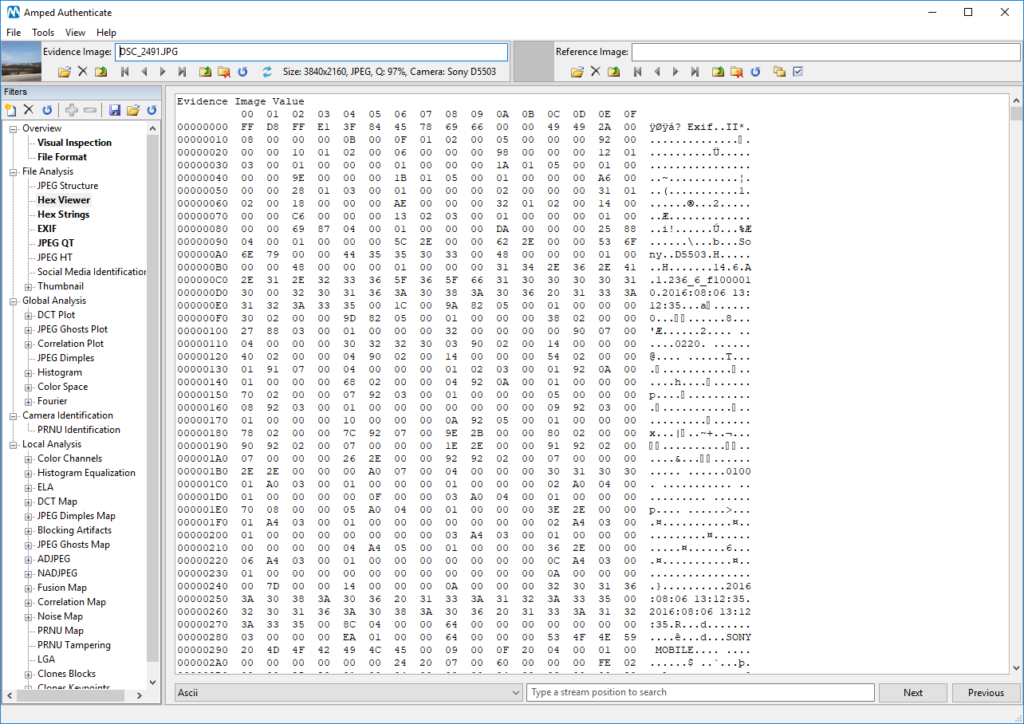
Hex Viewer is the most basic way: it is a hexadecimal viewer that allows you to inspect the binary content of the files. It is possible to perform searches based on an offset in the file, a hexadecimal value or an ASCII string. Let’s use the filter to analyze this image captured with my Sony Xperia Z1 smartphone:

As you can see below, the Hex Viewer shows the hex-code on the left, and the ASCII interpretation on the right column, whenever possible. There you can see quite a bit of human-readable information, such as “Exif”, “SONY MOBILE” and two date-times. Yes: that’s how Exif metadata are written inside the file! You can use the bottom bar to search for a specific offset (that is, the number of bytes since the beginning of the file) or, more pragmatically, to search for some ASCII string, such as “Photoshop”.
Why is all of that useful? Because someone may be trying to hide information, using the image file as an apparently innocent “carrier” to convey a secret payload. This technique is known as “steganography” – the Greek work steganos means “concealed” – since you don’t even notice that a secret message is being delivered (while in cryptography you can at least see the encrypted message).
If you find it boring to scroll through all the hex-code looking for some suspicious text, you may want to try the Hex Strings filter. It analyzes the whole bytestream and prints only sequences containing at least 5 printable ASCII characters, along with their offset, as shown below:
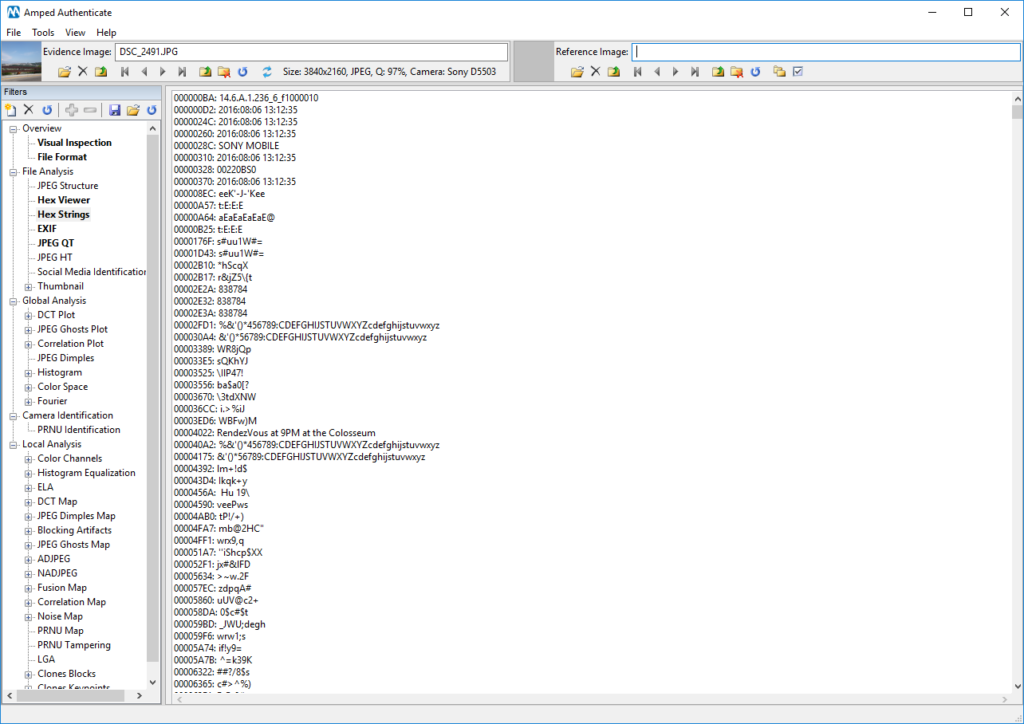
Did you notice anything strange in the Hex Strings output? If not, let us help you with a bit of zoom and color!
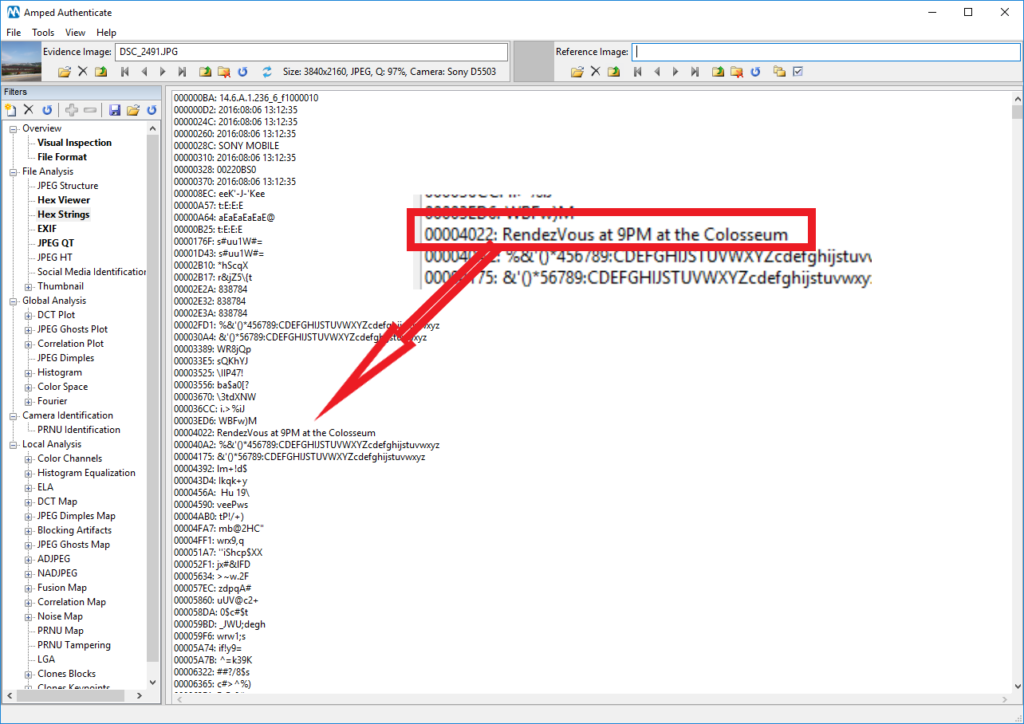
It seems like someone is dating in a very very subtle way! Whether or not this is suspicious, we’ll leave that to your investigators. (For the geeks: of course, you cannot just open a JPEG file and write your secret message in a random position, as you would likely corrupt the file. You should find a proper place, in this case, they opted for hiding the message just between the end of a “Start of Frame” and the beginning of “Define Huffman Table” blocks, as you can see by comparing the detected offset, 00004022, with those displayed by the JPEG Structure filter).
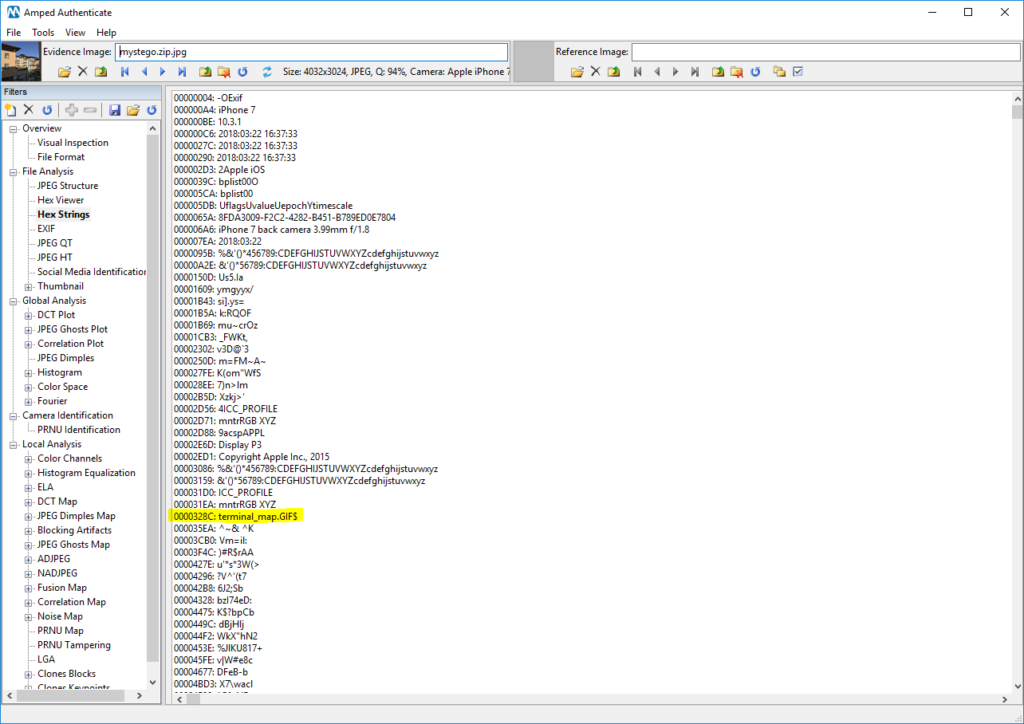
Be aware that someone could be hiding much more than text! For example, some months ago a popular tweet showed how you can hide all Shakespeare’s works inside a tiny image. Using the technique shown in the tweet and the related source code, we could easily embed a zipped Portland airport terminal map (44KB worth of data) into this image below (1.81MB)

A clever analyst could still find that something is going on thanks to the Hex String filter!
This week’s take away: always take a look at the Hex Viewer and Hex Strings filters, because even the streams can tell more than it seems!




