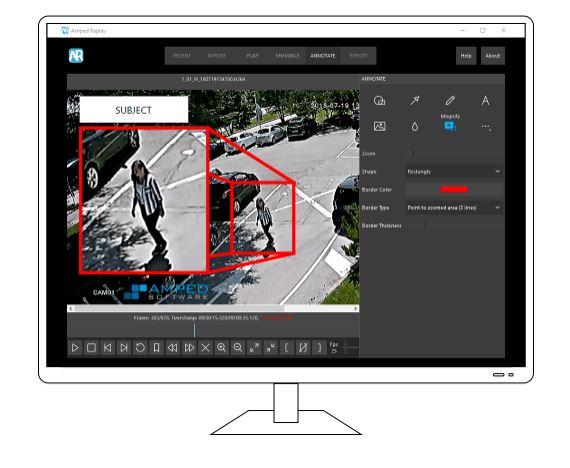
As you smart forensic analysts have undoubtedly noticed, last week there was no Tip Tuesday. Did we forget? Well, not really… We just realized that no Tip could stand the bright light shone by last Tuesday’s great announcement: the launch of Amped Replay, Amped Software’s newest solution for investigators and frontline officers! If you happened to miss that news read more about it here!
After that, you can enjoy this week’s Tip Tuesday!
If you are working in the digital forensic field, you are certainly aware of the importance of data integrity. Ensuring data integrity means to verify that the information you are working on remains unaltered during the whole process (including transmission and storage of data).
Unfortunately, when it comes to digital images and videos, integrity is more threatened than with other types of files. For example, if you rotate an image using your OS default photo viewer and then close it, the file will likely be overwritten without any advice. While in many cases the changes made to pixels may be “negligible”, the file will still change… which means its hash value will be different. And we know this could invalidate your whole analysis (in the end, another analyst cannot know why the hash is different, it’s just different).
At Amped, we take data integrity very seriously. Our software never overwrites nor moves the evidence file you are working with. But there’s more:
Amped FIVE provides you with a seamless way of checking data integrity straight inside your project. And this Tuesday’s Tip tells you how!
As you surely know, your Amped FIVE project is made of one or multiple chains. Each chain begins with a Loader, that brings an image or video into the program, and continues with a list of filters to be applied to your media. When you save and close the project, Amped FIVE only saves the media location and the list of filters to your drive. When you load the project back into FIVE, the media is retrieved from the saved location and then filters are applied. Now, if the media was changed in the meantime, the saved chain of filters will likely produce different results. Needless to say, this is something that contrasts with analysis repeatability!
Wouldn’t it be great if every time we load a project we could ensure that every input media has not been changed? That’s exactly what the Hash Code filter is for! You will find it under the Verify category.
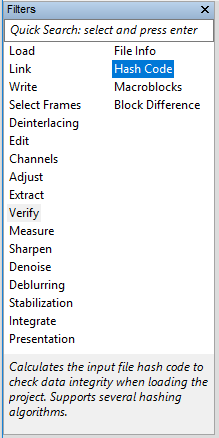
As soon as you click on it, a new filter will appear in your chain. It is a rather self-explanatory filter: if you double click on it in the History panel, you’ll see its settings, which show the current hash value and let you choose the hashing algorithm (one between MD5, SHA-1, SHA-256, SHA-384, and SHA-512).
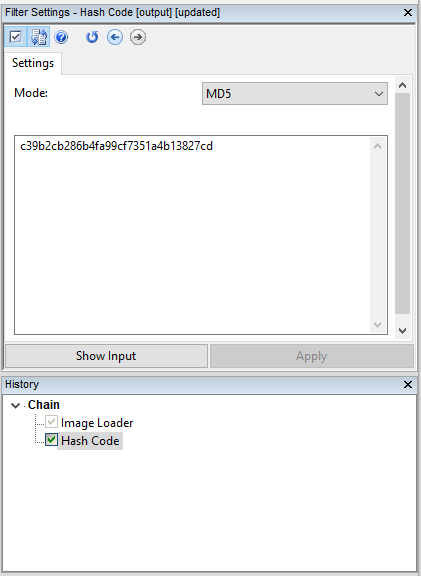
It’s all done! When you save the project, the hash value of the loaded media will be stored as well. When you re-open the project in Amped FIVE, the hash value of the input media will be evaluated and compared with the saved one. If it matches, nothing will happen. Otherwise, you’ll see this error:
Be aware that if one of the input files in your project fails the check, the project will not load, regardless of the number of chains it is made of… one more reason to ensure you don’t modify any of your evidence files! Of course, if you replace the altered file with the original one, everything will get back to working again.
We hope you enjoyed this Tip Tuesday! Stay tuned and don’t miss the next ones. You can also follow us on Twitter, LinkedIn and Facebook, YouTube : we’ll post a link to every new Tip Tuesday so you won’t miss any!




