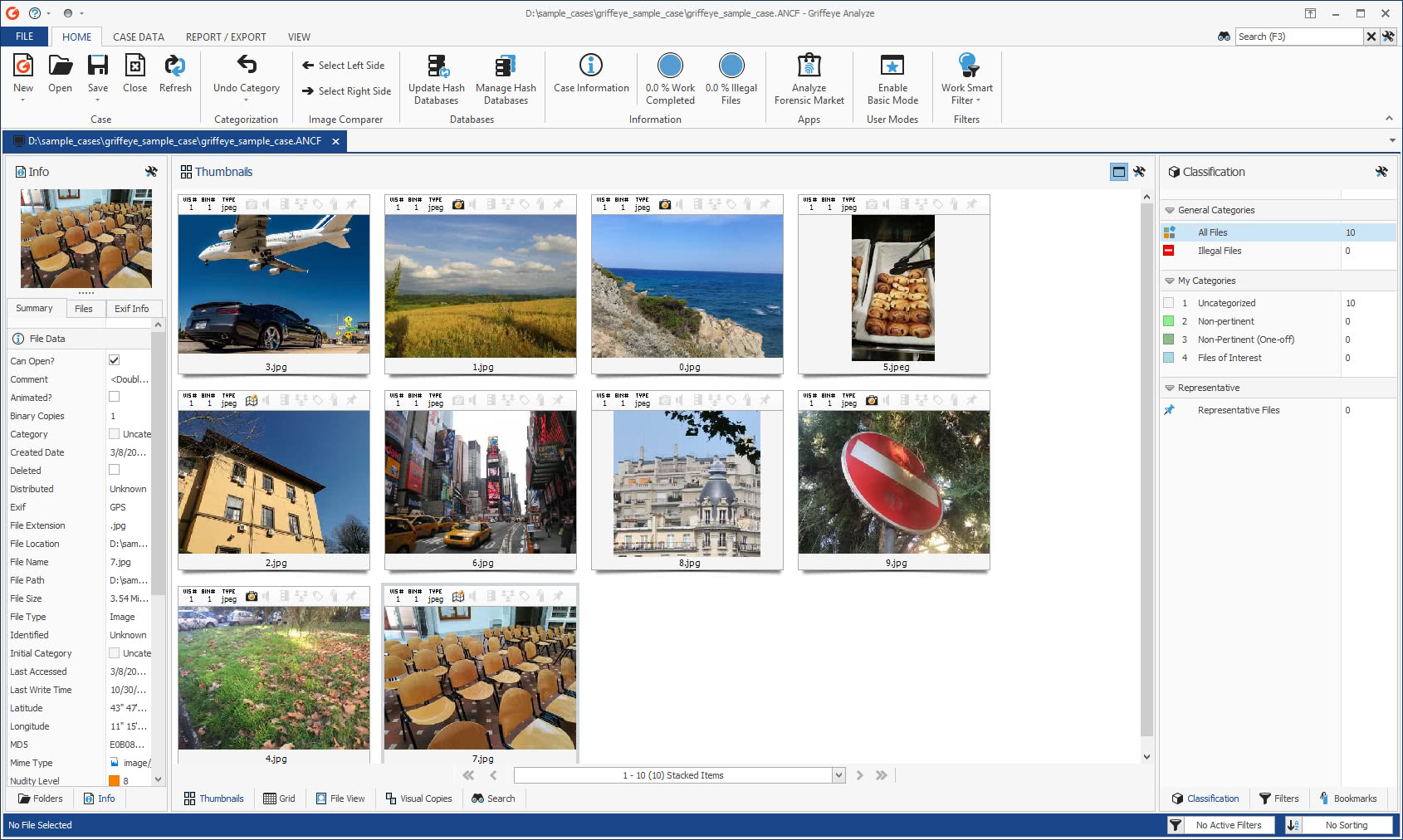
The partnership between Amped Software and Griffeye keeps growing and so does the integration between Griffeye Analyze DI Pro and Amped Authenticate. Analyze DI Pro is a media investigation software for handling large volumes of images and videos, filter irrelevant digital files, prioritize, correlate and identify the most pertinent material in investigations. It will let you scan and import data from a device or from a folder on your workstation. Once the import is complete, you can easily browse and intelligently sort/filter media.
In this post, we’ll take a look at what Griffeye Analyze DI Pro enables you to do when linked with the Amped Authenticate plugins. Let’s create a case and import a folder containing a few JPEG files.
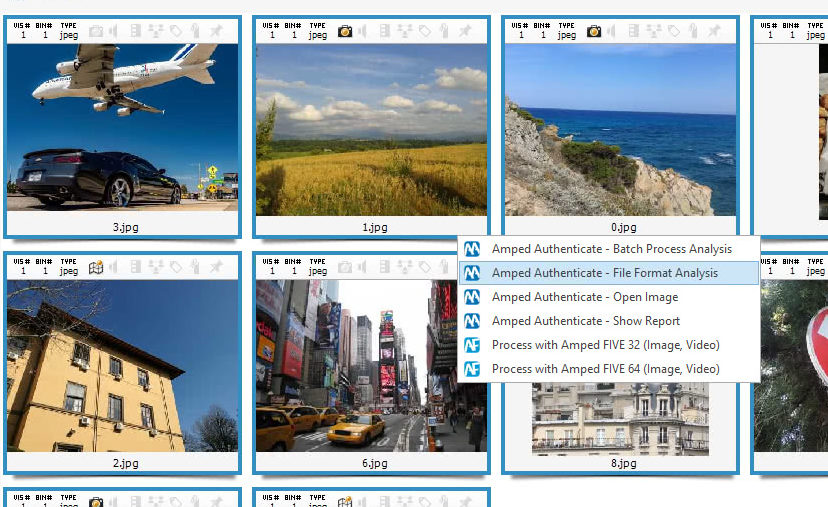
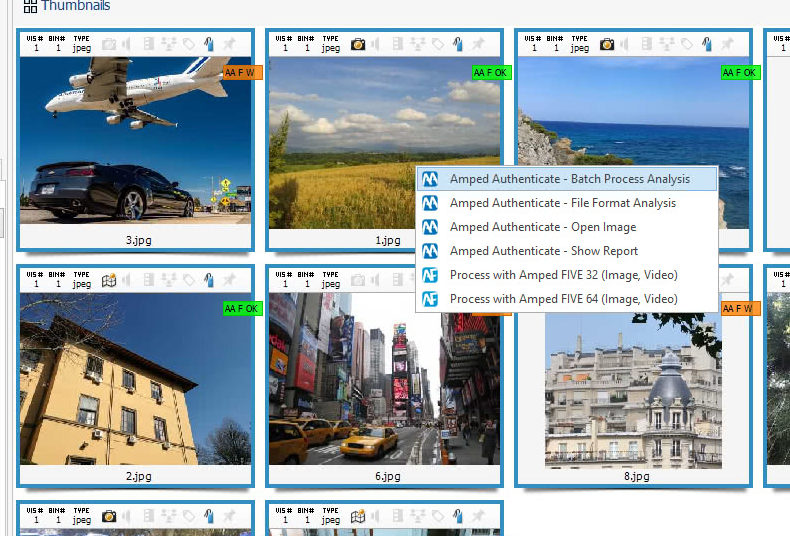
Analyze DI Pro lets you look at image metadata, and Amped Authenticate users know how interesting they are, but, we also know that a single image may contain hundreds of Exif metadata, and reading all of them is quite a boring job. Luckily, from the very same panel above we can call in Amped Authenticate File Format Analysis to automatically spot suspicious metadata. Once you installed Authenticate and the corresponding plugin in Analyze DI Pro, this is just as simple as right-clicking on one or all the images and then hit the “Plugin” voice and select “Amped Authenticate – File Format Analysis” from the pop-up list as shown below.
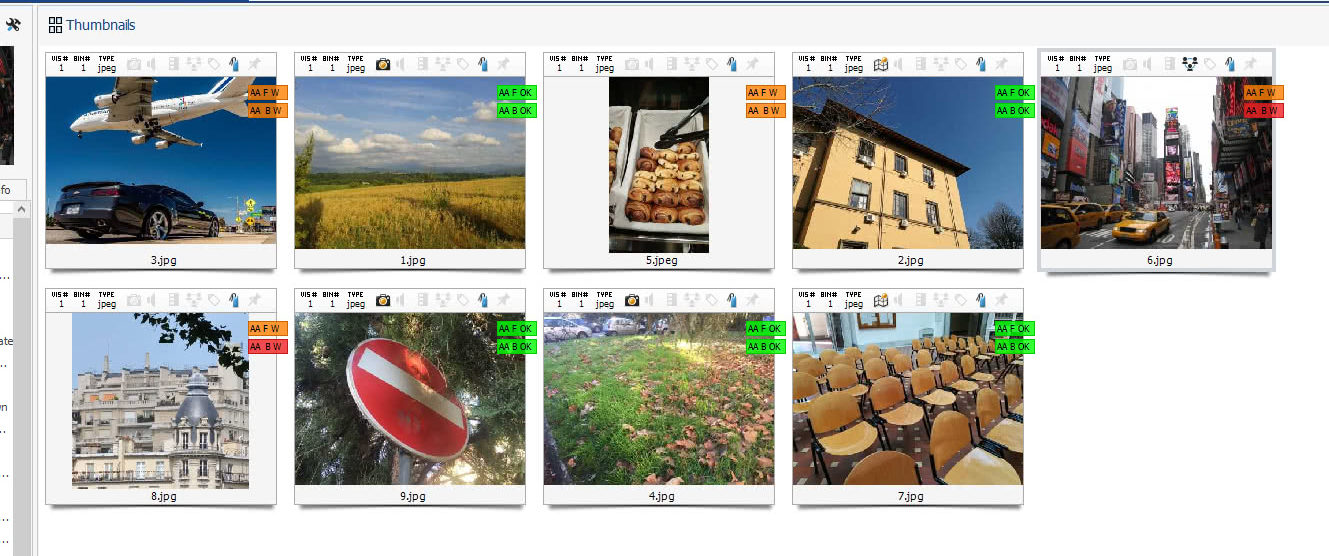
One click and Authenticate’s File Format Analysis rapidly scrutinizes selected files. File Format Analysis goes well beyond simple metadata analysis: more revealing properties like JPEG Quantization Tables, color subsampling, image resolution, aspect ratio and many others are checked to identify images that are unlikely to be camera original. After a few seconds, you’ll have results ready in the Analyze DI Pro interface, as the figure below shows.
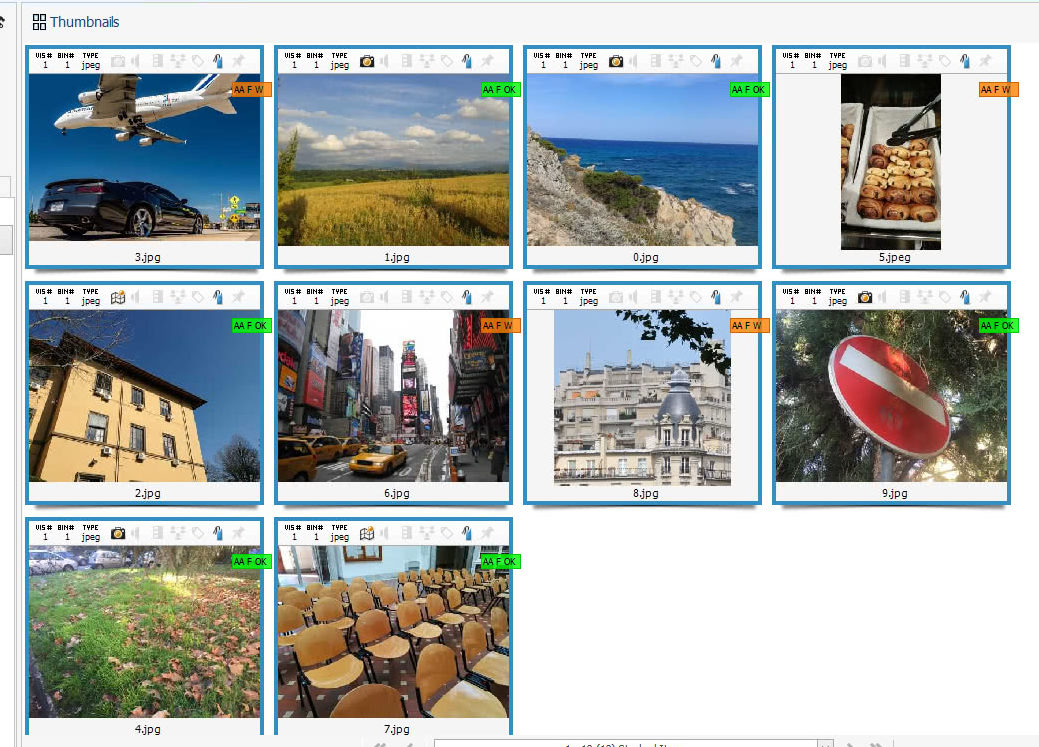
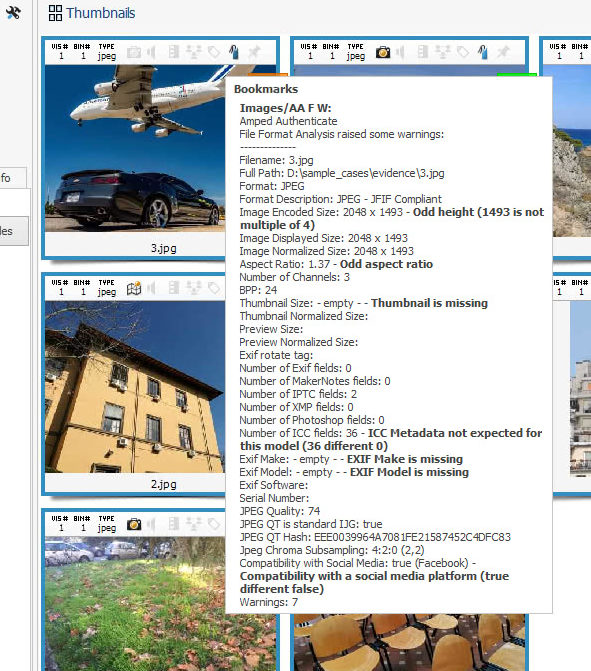
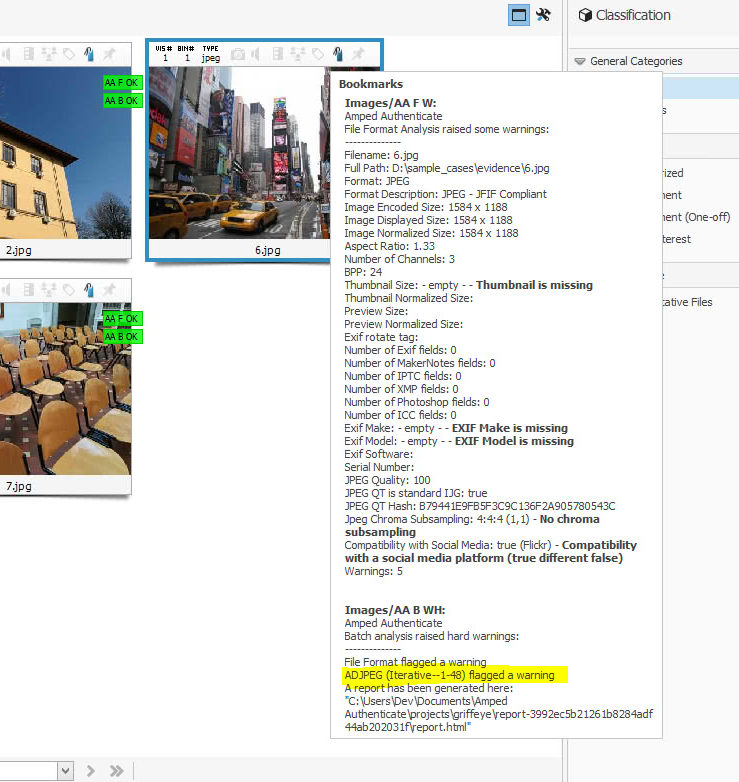
We see some images are tagged with an encouraging green label reading “AA F OK”, which stands for “Amped Authenticate file Format Analysis went OK“, meaning no warnings were raised. But some other images attract our attention because of that orange label reading “AA F W”, which means “Amped Authenticate file Format Analysis raised some Warnings”. If we scroll over the bookmark icon with the mouse, we’ll see this brief report from File Format Analysis:
The purpose of File Format Analysis is to identify image features that are not common to camera original images. When found, problematic elements are accompanied by a boldface comment stating why Authenticate flagged a warning on them. In the case above, we see the airplane image is problematic for several reasons: the resolution and aspect ratio are odd, some expected Exif metadata are not there while we have unexpected ICC metadata and, most prominently, the image seems compatible with a Social Media Platform (namely Facebook).
At this stage, the integration between Analyze DI Pro and Authenticate already suggested that four of the ten images are likely altered since the time of creation, which means their integrity is compromised. Of course, this doesn’t mean they are not authentic: just because an image comes from Facebook, it does not mean we can’t trust its message.
This is where another piece of the integration comes in handy: we can ask Authenticate to make a full Batch Process Analysis of the files. Of course, this will take longer than the simple File Format Analysis, but will also tell us a lot of details about the images’ digital history. Let’s call in Authenticate as shown below:
We can go grab an espresso now, while Authenticate deeply scans every file, presenting us with a new set of labels upon completion.
We see that:
- all images that were assigned a green label during File Format Analysis also get a green label after the thorough Batch Process Analysis. This fact increases our confidence in their integrity and authenticity.
- two of the orange-labeled images get another orange label reading AA B W, indicating that “Amped Authenticate Batch Analysis raised some soft (orange color) Warning”. This was expected since the File Format Analysis is a subset of the Batch Process Analysis, so we’ll get at least the same degree of warning we had before.
- the remaining two images get a red label reading AA B W, indicating that “Amped Authenticate Batch Analysis raised some hard (red color) Warning”. It means Authenticate found something suspicious at the pixel level, a threat to image authenticity that deserves attention. If we click on the bookmark we’ll see which tools are responsible for the warning.
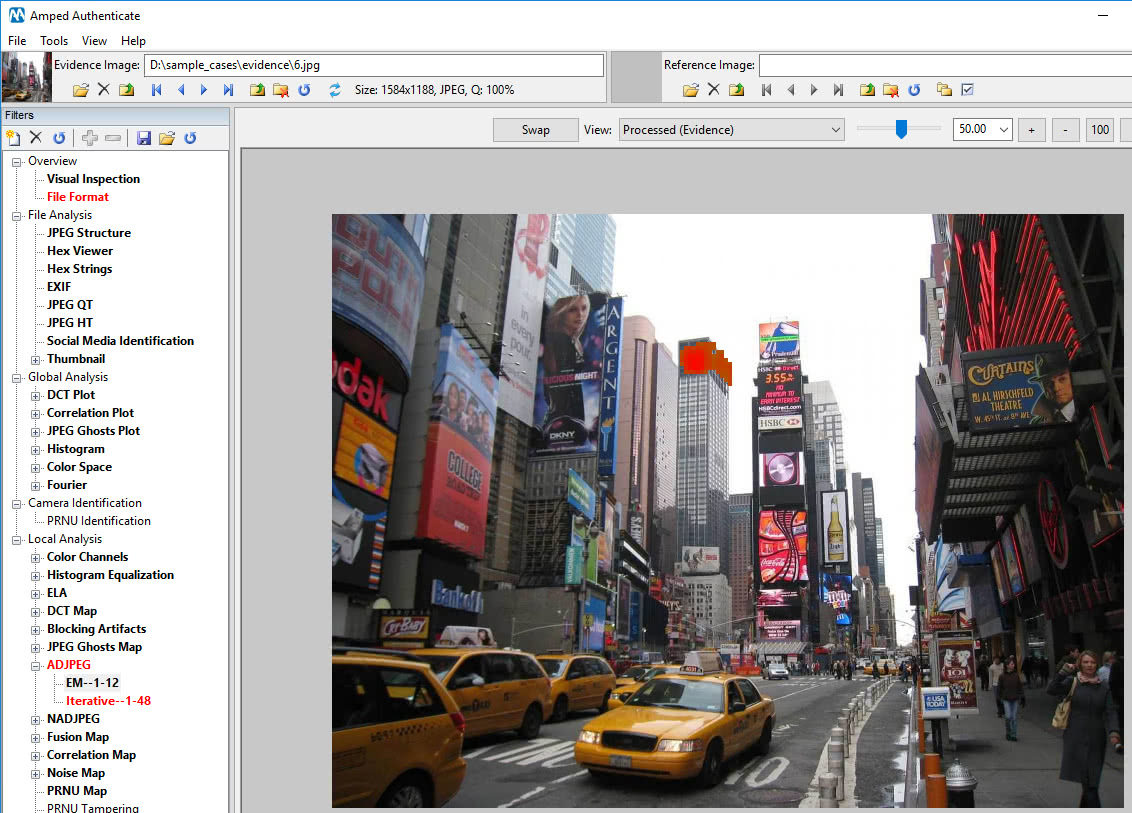
As we can see below, for the selected image the ADJPEG (Aligned Double JPEG Analysis) flagged the warning. To find out why, we can right click on the image and open it in Authenticate. Authenticate will open, load the questioned file and all its cached filters, so we don’t have to wait for any re-processing. In our case, we see that there’s something strange at the top of the skyscraper in the background.
If we are allowed to do so, we can send the image to Google reverse search (using Authenticate’s Tools->Search similar images on the web) and look for visually similar images on the web. It only takes a few seconds to spot the original picture!
And that’s it! In a few clicks, we acquired and organized media from a folder (okay, it was just 10 images in this case, but Analyze DI Pro works with millions as well), we rapidly scanned them, identified those whose authenticity was questionable, localized the manipulated region and, in this specific case, we also used the web to find the original picture.
We hope we’ve been able to show you how the synergy between three market-leading products (Analyze DI Pro for media triage and prioritization, Amped Authenticate for integrity and authenticity analysis, and Google for reverse image search) can empower the digital forensic analyst and make his work so much easier!