During a recent workshop on image authentication, I ran a few practical sessions. One concentrated on the changes that online services and social media platforms make to the images that we upload. It turned out to be an interesting experiment that has had some structured research over the past few years.
These are excellent starting resources when developing any internal Standard Operating Procedure:
A Classification Engine for Image Ballistics of Social Data: https://arxiv.org/abs/1610.06347
A Forensic Analysis of Images on Online Social Networks: http://ieeexplore.ieee.org/abstract/document/6132891/
Why is this important?
When identifying the reliability of an image, we often must understand what has changed in an image. Some changes occur automatically, and sometimes unknowingly, by a service or program. If changes are understood, we may be able to identify changes that are explainable.
The session started with the taking of original images. These images were then stored online or shared via services such as Facebook and Twitter. These images were then accessed and recovered.
The final stage was a comparison between the original image and the image that had been through the various services. This comparison stage was conducted in Amped Authenticate.
The outcome of this session was a clear understanding of the complexities of online data sharing and storage when it comes to authentication and originality.
I thought this was worth sharing as you may find it useful when attempting to replicate changes or understand why differences occur.
The first challenge we came across was identifying, not only the source of the image but what was used within the source. There were differences when using a web browser to upload an image when compared to using an app.
As can be seen from the following graphic, we identified 3 main sources. Within each were several different methods to facilitate the upload or sharing procedure.
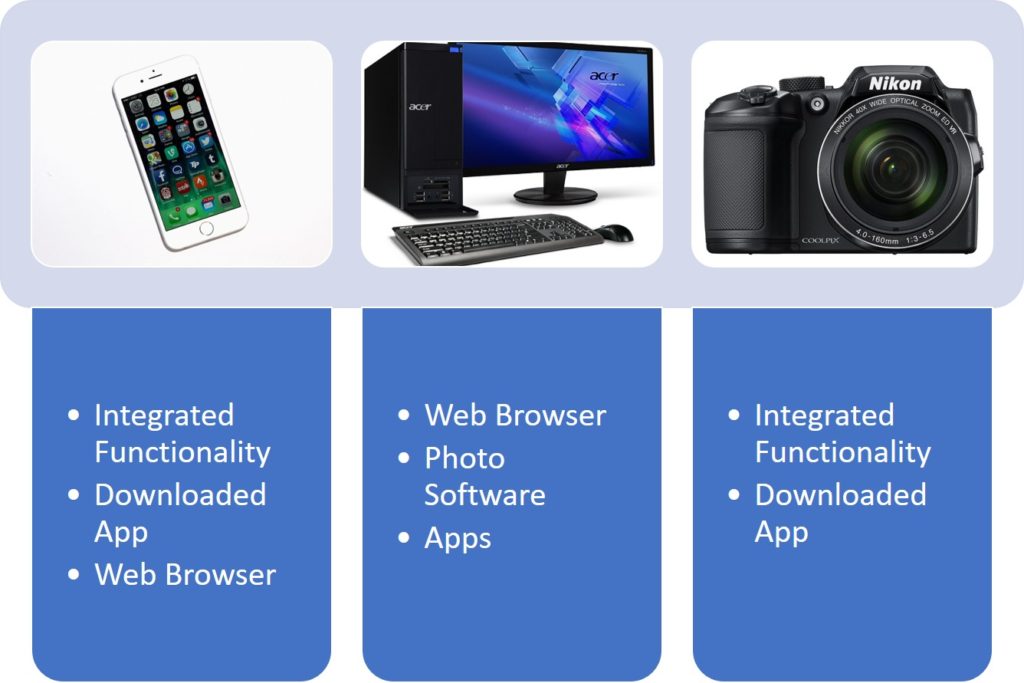
From there we have the service that holds our image. There are many different services and each one has different methods and user options. Some of those used in our experiment can be seen below.

Finally, we have the many options for the acquisition of the image that now resides online.
How the image is recovered forms the final throw of the dice.
We identified that there were two main options: the presentation of the image, and a dedicated download facility.
With the presentation view, the differences appeared in what method was used.

The result of this experiment clearly shows that it is now not possible to form a simple process map from start to finish. There are many variables involved and this does not consider any software functionality in service updates or versions.
Our initial aim was to understand differences between services. However, it showed more clearly how difficult it is to replicate an image creation process if one part of the process is unknown.
I hope that this gives you some considerations if you plan to attempt an image creation replication. There are many methods and options – it’s not going to be easy!




