A few months ago we launched a pretty bulky Amped Authenticate update with several new filters and features. In this post we’ll explain how the ADJPEG and NADJPEG filters work and how to use them.
When an image is first compressed using the JPEG format, there is a uniformity to the Discrete Cosine Transform (DCT) coefficients throughout the image. If an object is placed into the image and then it is re-saved, there will two different levels of compression.
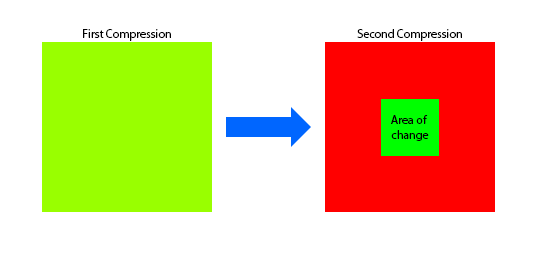
As is illustrated in the graphic above, the first block has a single level of compression. The second block, which has had an object pasted in, is mainly red as all of the original image has undergone another level of quantization. Only the new object has a single level as it was different than before.
Let’s see what this looks like in reality with a couple of examples:
On the right is an image of some floor tiles. The question being asked of me, as the analyst, is to identify any evidence of manipulation which could call into question the authenticity of the image.
As is always the case in authentication, it is good practice to utilize all methods open to you, and not rely on a single filter result.
After a visual Inspection of the file, revealing no obvious issues, Metadata File Analysis flagged up a number of warning signs regarding how the image was last saved. A lot of these can be manually edited to hide certain tell-tale signs so again it’s wise to never use this alone.
For this post, I’m going to head straight to the new filters now, in order to concentrate on their results.
The first is ADJPEG, and this is for detecting signs of double JPEG compression where the 8 x 8 pixel blocks are aligned. Block alignment occurs when both JPEG compression’s are aligned in the same manner. If they are Not Aligned, such as is shown in the graphic below, then another filter may be required… and we’ll come onto that one in a bit!
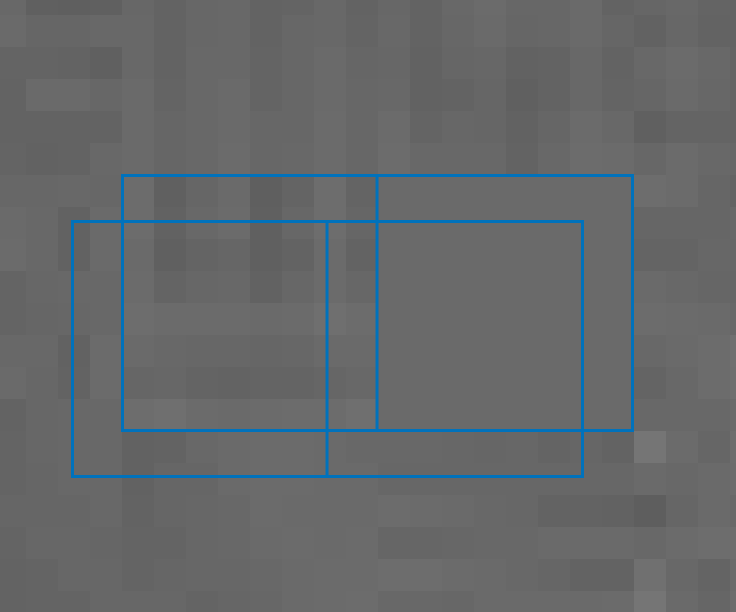
After running ADJPEG (Aligned Double JPEG), across my tile image, the result immediately causes some concern.
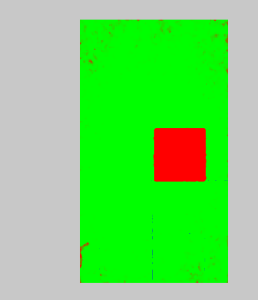
Straight away, we see a visualization of an area that is suspect. We are seeing an area that has undergone two levels of compression.
Obviously, in a real case, we would not know exactly, how or why the image was manipulated. However, it is possible to scientifically prove that the area shown in red has undergone different compression stages.
Before we move onto the next filter, what about the true image, what was hidden?….
If we now look at the original image, its possible to see that an item was on the floor. Another picture of a tile has been taken and copied over the top of the original image, thereby hiding the item.

Let us now have a look at a different angle, in order to understand the NADJPEG filter. This Filter is for those circumstances where the areas of manipulation are Not Aligned on the 8 x8 blocks.
When the filter is applied, it will scan the 8 x 8 pixel blocks, detecting the quantization coefficients.
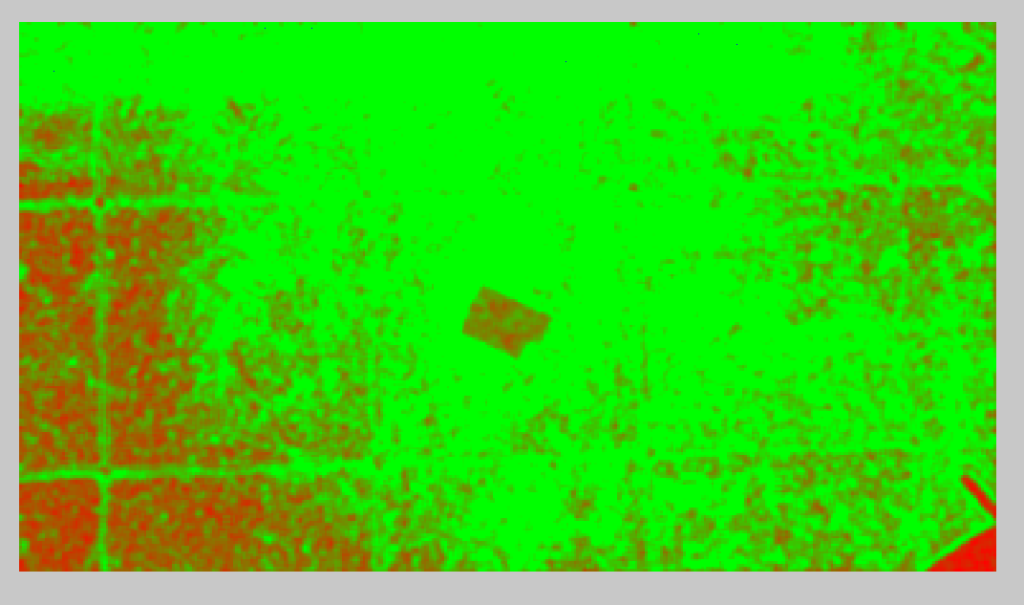
Immediately, I can see the outline of the notepad, but why is that shown to have double quantization. The plain white area should only be quantized once.
Well, as you may have guessed, that notepad was cut and pasted from the earlier image. The original image never had the notepad there. Go back and take a look at the size of the notepad to the tile in the first set of images!
If we run the same filter on an image where the notepad was actually there…
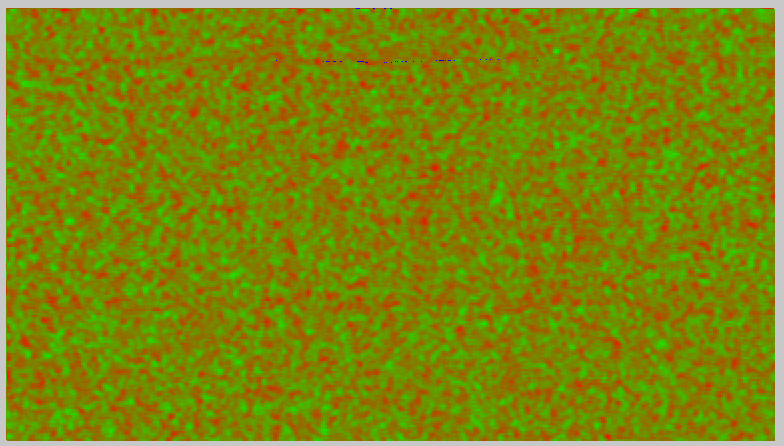
and this was the image…

It’s extremely important when conducting this sort of analysis to perform tests in order to replicate what modification you believe may have taken place.
At this point then, let’s move onto the last new Filter, The Fusion Map. This is a clever mix of the JPEG Ghost Filter and the new Aligned and Non-Aligned Double JPEG Filters.
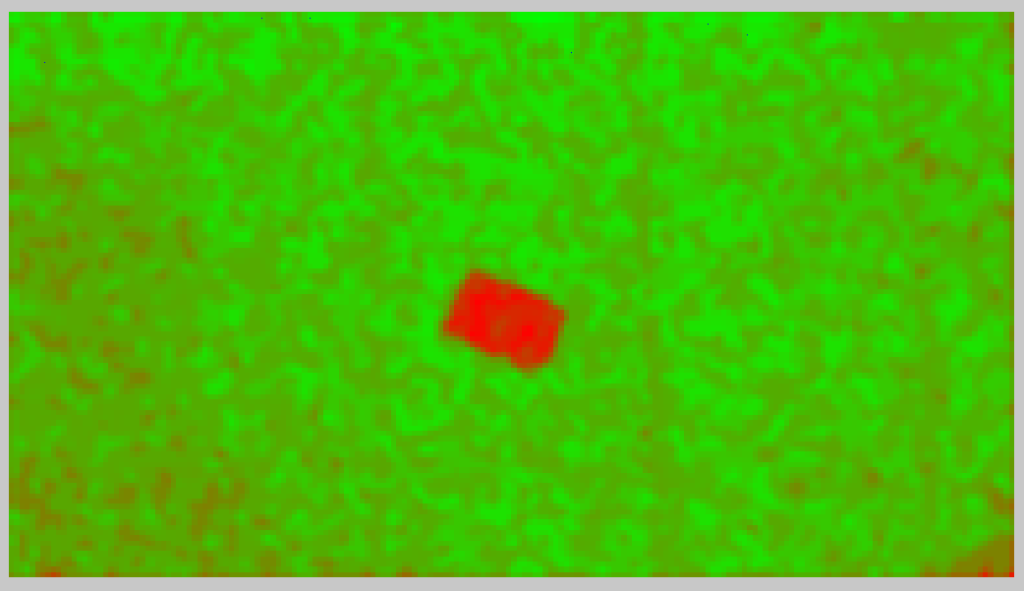
It gives a very clear representation of the suspect area.
These new filters build onto the established filters already present. However, there are manipulation techniques and stages that can hide compression noise and error detection. Using these new powerful algorithms to analyse each block’s Discrete Cosine Transform domain, the filters can increase a trained analysts chances of identifying manipulation and thereby question an images authenticity.