Dear Tip Tuesday fans, welcome! This week’s Tip is dedicated to showing the power of the widely loved Amped Authenticate‘s Camera Identification filter. Based on sensor pattern noise analysis, this filter is one of the most reliable and robust in the image forensics field, where “robust” means it may still work even after the image has gone through significant processing. To demonstrate this in practice, we’ll see how the Camera Identification filter often works even on images downloaded from Facebook, which has a dramatic impact in terms of applications.
Source identification is the task of obtaining information about the originating device of a given image. Several levels of analysis are possible:
- Class level, e.g., we want to know whether the investigated image is from a camera, a smartphone, a scanner, or it is computer-generated… ;
- Model level, that is, understand the brand and model of the device which captured the image;
- Exemplar level, which means associating the image to the exact device used to generate it (like it is done for bullets with guns, and this is why this latter point is also known as camera ballistics).

Usually, the more specific a question is, the more difficult it is to answer. In this case, however, the opposite is true: the most reliable techniques are available for source identification at the exemplar level! This is possible thanks to a group of researchers who discovered that each camera sensor is affected by a kind of noise, called Photo Response Non-Uniformity (PRNU Analysis), that turns out to be unique to that exact sensor. This noise is imperceptibly left in every image captured by the camera.
The basic idea, then, is that we can estimate what we call the Camera Reference Pattern (CRP) from a bunch of images that we know come from the camera (50 is a good number, but less could suffice). When asked to verify whether a test image comes from the camera, we “compare” the noise in the image with the available CRP: if a good match is found, we say we have “Positive compatibility”, otherwise we opt for “Negative compatibility”.
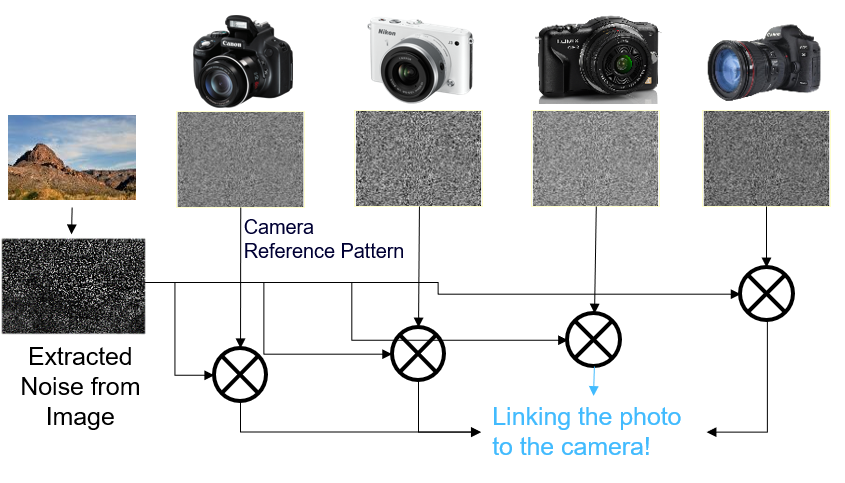
This kind of analysis was proved to have very good specificity: it is highly improbable to obtain a “Positive compatibility” if the test image does not come from the camera that originated the CRP. The sensitivity of the test (which means, the ability to call a “Positive compatibility” for images that indeed come from the camera) is also excellent when working with camera original images. But what if the image was indeed captured by the camera and then processed? Well, it depends on what you do. Slight JPEG compression will do little harm, as well as slight resizing. You can find some details about Amped Authenticate’s implementation of this analysis in this post, and a detailed experimental validation of our implementation in this other post.
Today, we’re testing Authenticate’s PRNU Identification in a very interesting case: images downloaded from Facebook. Facebook, like many other Social Media Platforms (SMPs), will process your images upon upload. Normally, they will be down-scaled by a good amount (depending on the original image resolution) and JPEG compressed quite aggressively. It’s understandable, they have to transfer terabytes of images every hour. Will PRNU noise survive this?
We used images from a publicly available dataset called VISION, and we selected three smartphone models:
- Apple iPhone 6 Plus
- Sony Xperia Z1 Compact (formal name: D5503)
- Huawei P8 (formal name: GRA-L09)
For each model, we created the CRP using 50 original images, and then tested it against 100 Facebook images, 50 of which originated from the model and 50 from other various models in the VISION dataset, including other smartphones from the same producer. Below you see the results in terms of the number of true positives and true negatives: as expected, we never mistakenly call a “Positive compatibility” on images that are not from the same device as the CRP. As to the true positive rate, we get 100% correct detection for the iPhone 6 Plus and the Xperia Z1 Compact, while we miss almost half of the images for the Huawei P8. Probably, this device leaves a less marked PRNU noise in its pictures.
| Device | True Positives | True Negatives |
| Apple iPhone 6 Plus | 50/50 (100%) | 50/50 (100%) |
| Sony Xperia Z1 Comp. | 50/50 (100%) | 50/50 (100%) |
| Huawei P8 | 26/50 (52%) | 50/50 (100%) |
| Average | 126/150 (84%) | 50/50 (100%) |
To make things even harder, we repeated the experiment, this time generating the CRP using Facebook images and testing on the same set used before (of course, we’re not using the same images for CRP creation and testing, that would be cheating!). Results (shown below) are very, very encouraging!
| Device | True Positives | True Negatives |
| Apple iPhone 6 Plus | 50/50 (100%) | 50/50 (100%) |
| Sony Xperia Z1 Comp. | 47/50 (94%) | 50/50 (100%) |
| Huawei P8 | 9/50 (18%) | 50/50 (100%) |
| Average | 106/150 (71%) | 50/50 (100%) |
Although we did not make an extensive validation (the VISION dataset is freely available, if you want to try yourself!), what we’ve seen in this Tip is enough to give us good hope about the possibility of associating Facebook images to the device that captured them using sensor noise analysis! Think about how important this could be in cases where social media are used for harassment, bullying, blackmailing! PRNU Identification is a true weapon in your rich arsenal called Amped Authenticate.